Business Continuity Management / Disaster Recovery , Critical Infrastructure Security , Cybercrime
Ransomware: Alphv/BlackCat Is DarkSide/BlackMatter Reboot
Group Perpetually Rebranding After Numerous Encryption, Target-Selection Mistakes
In news that should shock no one, security researchers say the ransomware operation known as Alphv - aka BlackCat - appears to be a reboot of the notorious group known as BlackMatter, which was itself a rebrand of DarkSide.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
"While Alphv claim to be former DarkSide/BlackMatter affiliates, it's more likely that they are DarkSide/BlackMatter but attempting to distance themselves from that brand due to the reputational hit it took after making an error that cost affiliates multiple millions of dollars," tweets Brett Callow, a threat analyst at security firm Emsisoft.
The BlackCat moniker was given to the ransomware operation by the security researchers known as MalwareHunterTeam last December, after they spotted attacks by the then-unnamed group, which began last November.
There is a very interesting new Rust coded ransomware (first ITW?), BlackCat.
Another one used to encrypt companies' networks.
Already seen some victims from different countries, from the second half of past November.
Also look at that UI. Back to '80s?
@demonslay335 @VK_Intel pic.twitter.com/YttzWWUD3c— MalwareHunterTeam (@malwrhunterteam) December 8, 2021
Like its prior incarnations, Alphv/BlackCat uses a ransomware-as-a-service business model, in which operators or administrators build and maintain the ransomware. Pre-vetted business partners, aka affiliates, download a personalized version of the crypto-locking malware via a Tor-based portal and use it to infect victims. Affiliates appear to be promised an 80% to 90% cut of every ransom that gets paid, with the rest going to the operators, says Palo Alto Networks' threat intelligence team, Unit 42.
Critical Infrastructure Hit
Whatever name the ransomware group has been operating under, it has made some monumental mistakes.
Arguably, one of its biggest errors was its malware being used in a May 2021 attack on Colonial Pipeline Co. in the United States, which sparked a political firestorm. Straining credulity, given the ransomware business model, DarkSide blamed an affiliate for having gone rogue.
Despite the attempted marketing spin, the operators walked away substantially richer. Colonial Pipeline paid it a ransom of 63.7 bitcoins - then worth $4.4 million - in return for a decryptor. Colonial Pipeline CEO Joseph Blount told U.S. lawmakers last June that the decryptor hadn't worked as advertised and that it had been quicker and easier for his company to restore systems from backups.
The FBI, however, did manage to recover $2.3 million of the ransom payment, possibly because the bureau gained access to a wallet into which an affiliate's share had been moved.
That and other attacks led U.S. President Joe Biden to issue Russian President Vladimir Putin an ultimatum: Unless Moscow did more to crack down on ransomware groups operating from inside Russia, Washington reserved the right to target them directly.
Perhaps feeling the heat, DarkSide went dark shortly thereafter, as did rival REvil, aka Sodinokibi. But DarkSide quickly relaunched as BlackMatter in July 2021.
String of Mistakes
In both the DarkSide and BlackMatter eras, however, developers made some serious encryption implementation errors in their malware, which allowed security researchers to quietly help victims decrypt their systems without having to pay attackers for a decryptor. In the DarkSide iteration, Emsisoft says the group's malware included encryption errors from Dec. 12, 2020, to Jan. 12, 2021, when the criminals fixed the problem, likely after having investigated a massive dip in ransom payments.
Meanwhile, after rebooting last July, "BlackMatter introduced a change to their ransomware payload that allowed us to once again recover victims' data without the need for a ransom to be paid," Emsisoft CTO Fabian Wosar wrote in a blog post last October, when the errors came to light publicly (see: Memo to Ransomware Victims: Seeking Help May Save You Money).
Wosar said that "as soon as we became aware of the gang's error, we quietly reached out to our partners, who then assisted us in reaching as many victims as possible before they paid BlackMatter's ransom." Cue what must have been a massive dip in the group's profits.
Fresh Approach to Malware Development
In response, DarkSide/BlackMatter appears to have fired its development team and hired a new one, going dark last November before launching later that month as Alphv, aka BlackCat.
The group claims otherwise. Dmitry Smilyanets, an analyst at threat intelligence firm Recorded Future, on Friday published an interview with Alphv Support, who's one of the operation's administrators. Alphv Support claims that the Russian-language operation is comprised of former "adverts" - aka affiliates or advertisers - of numerous operations.
But Callow and others dispute that claim, saying extensive evidence suggests BlackCat is simply the latest DarkSide rebrand.
"Intel from various sources indicates that the actors behind BlackMatter may have replaced their dev team after we discovered and exploited a weakness in their ransomware, and the new team created Alphv," Callow told Recorded Future in response to Alphv Support's claims.
The presence of a new development team would help explain why BlackCat is now the first major ransomware operation to be developing its malware using the Rust programming language.
Most malware developers code in C, C++ or Go, researchers from threat intelligence firm Digital Shadows' Photon Research Team have told Information Security Media Group. Rust "features good performance but more crucially, secure memory management, which reduces the probability that the malware will crash before it can be executed," and it's likely that more ransomware developers will switch to Rust, they say.
Growing List of Victims
Alphv/BlackCat already appears to be relatively active. The operation runs a dedicated data leak site on which it can list victims who have not paid a ransom, to try and pressure them into paying.
It's not clear what fraction of Alphv/BlackCat's victims end up being posted to the data leak site. Cybersecurity firm Group-IB estimates that only 13% of victims of a ransomware operation that runs a data leak site will end up being listed there. Accordingly, there's no accurate count of how many organizations the group has hit or how many victims have paid. But based on a count by Unit 42 of victims posted to data leak sites last December, Alphv/BlackCat listed the seventh-greatest number of victims.
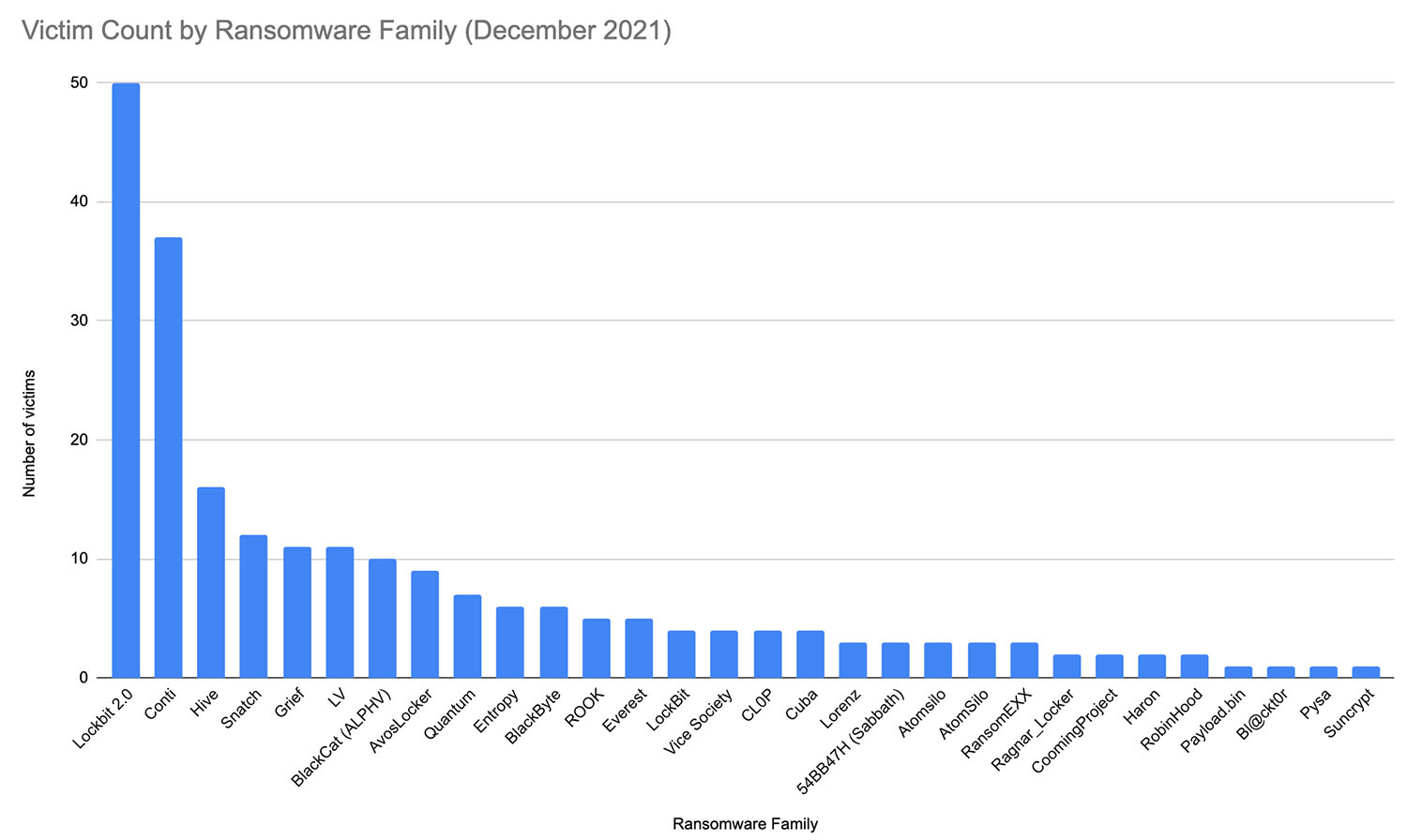
In the past week, Alphv/BlackCat's data leak site has featured four new victims, including an outsourced call center in Hong Kong, a Chicago-based bank, a French meat processing company and an Indian industrial automation software vendor, according to Israeli threat intelligence firm Kela.
Researchers at security vendor SentinelOne say the operation has been making initial ransom demands in the range of $400,000 to $3 million, although victims who choose to pay might be able to negotiate a lower amount. Victims can pay in privacy-preserving monero or else bitcoin, although choosing the latter will add 15% to the ransom amount, which is not unusual.
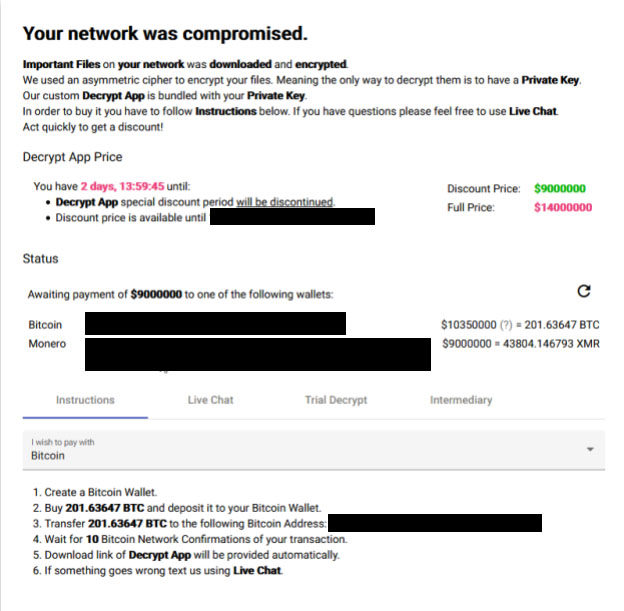
For negotiating a ransom payment, Alphv/BlackCat also maintains an "Intermediary" page designed for use by ransomware-negotiation firms to use, Bleeping Computer reports.
Alphv Support told Smilyanets that the attackers welcome working with negotiators because they "simplify the process." "They have their own personal discounts that can vary between 20% and 40%, and the entire recovery process takes no more than 24 hours from the moment of the first contact," he says.
Critical Infrastructure Hits Continue
One outstanding question is whether ransomware-wielding attackers have learned any lessons from past missteps. Many experts, for example, suspect that instead of big game hunting - meanwhile hitting big targets in search of massive ransoms - groups will instead try more mid-game hunting, seeking smaller victims to help them stay more under the radar of law enforcement agencies.
After hits by Conti on Ireland's national healthcare system last May, followed by DarkSide attacking Colonial Pipeline and REvil hitting the world's biggest meat producer - among many other attacks - many ransomware operations claimed that they would prohibit the targeting of critical infrastructure, healthcare and other sectors.
For example, when asked about the presence of a healthcare sector victim on its data leak site, Alphv Support told Smilyanets: "We do not attack state medical institutions, ambulances, hospitals. This rule does not apply to pharmaceutical companies, private clinics." Then again, ransomware-wielding criminals regularly lie.
Meanwhile, BlackCat has not yet taken credit for a large-scale ransomware attack that disrupted operations at 17 oil terminals across Belgium, Germany and the Netherlands. But German newspaper Handelsblatt reports that German cybersecurity officials have attributed the attack to BlackCat.
Hence after the disastrous hit on Colonial Pipeline, the DarkSide - aka BlackMatter, BlackCat/Alphv - operators don't appear to be actively avoiding attacks that might affect critical infrastructure.
Maybe it's time for another rebrand?











