COVID-19 , Governance & Risk Management , Remote Workforce
The New Enterprise Risk Management Strategy
Alan Ng of China Taiping Insurance on How COVID-19 Has Changed the Game
Security practitioners used to focus on the Confidentiality, Integrity and Availability - or CIA - triad as the foundation of cybersecurity. But as COVID-19 drove more digitalization, more risks transformed into technology and cyber-related risks as we leveraged more technology to drive businesses to reach more customers.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
The old risk mitigation strategy and controls were inadequate to reduce the risk effectively. So, as our adversaries constantly evolved and came up with new techniques every day, we as security professionals also had to adapt to meet the challenges of cybersecurity.
We used to traditionally secure the perimeters, assume internal networks were secured and hold the virtual defense lines. But the massive adoption of cloud-based solutions and work from anywhere, anytime has made us perimeterless - or borderless - allowing access from any device in a frictionless manner. This, in turn, is generating a huge amount of data in the cloud.
The demand to protect anywhere, anytime access to digital capabilities requires security to become software-defined - to be able to adapt quickly, and cloud-delivered - to leverage its technology and scalability to force changes in security architecture and strategy. It even affects the vendor/technology selection criteria and requirements.
We also have to embrace a new strategy to defend our organizations. I believe the following three new paradigm shifts in cybersecurity are worth a deeper look and consideration to achieve a higher cyber resiliency and to approach cybersecurity differently.
Distributed, Immutable and Ephemeral Triads
The Distributed, Immutable and Ephemeral - or D.I.E - triad, presented by Sounil Yu, CISO and head of research at JupiterOne, offers a new paradigm to make attacks irrelevant.
In each of the eras, we faced new challenges that directly undermined our ability to identify, protect, detect or respond. And so we had to develop new solutions to help us overcome each of these challenges. The prior era solutions did not solve the current era’s problems.
—Sounil Yu
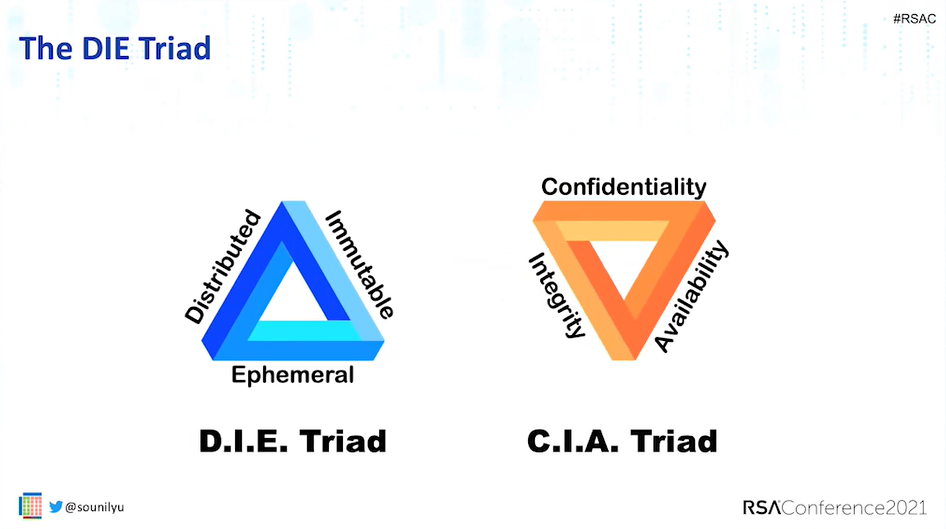
As more applications, systems and infrastructure are now designed and built in a highly distributed and always available manner, they are highly resilient, fault tolerant, elastic and scalable - in the cloud and/or on-premises. This help addresses the availability aspect of the C.I.A. triad.
Because the applications, systems, and infrastructure are created to be immutable, small changes are detected very easily. This removes the need to maintain integrity. Integrity problems occur when we have the ability to make changes, either intentionally or unintentionally, that are very hard to detect. That affected the integrity aspect of the C.I.A. triad.
Being ephemeral makes the applications, systems, and infrastructure transient, or short-lived. That disrupts the persistence that a malicious attack requires to affect the confidentiality aspect of the C.I.A. triad and makes the window of opportunity for the attacker much smaller.
Chaos Is Good
Chaos Engineering originated at Netflix, while the company was moving to the cloud, and gave birth to the Principles of Chaos Engineering to improve resiliency.
Chaos Engineering is the discipline of experimenting on a system in order to build confidence in the system’s capability to withstand turbulent conditions in production.
—Principles of Chaos Engineering
With the foundations of Chaos Engineering, the principles can be applied to security engineering as well.
Security Chaos Engineering is the discipline of instrumentation, identification, and remediation of failure within security controls through proactive experimentation to build confidence in the system’s ability to defend against malicious conditions in production.
—Aaron Rinehart
According to Rinehart, the co-founder and CTO of Verica, Security Chaos Engineering is a way to approach security differently. The idea is to test the resiliency of the security controls continuously and automatically in the face of chaos - or simulated real-life events on real production systems in a controlled manner - without affecting other systems. This helps security practitioners build confidence and learn about and improve the resiliency and effectiveness of those controls over time.
Trust No One, Verify Everything
Zero Trust was created by John Kindervag when he was with Forrester Research to address the broken and outdated trust model of assuming everything within the perimeter can be trusted.
It is a security concept centered on the foundation that organizations should not by default trust anything or anyone internally or externally, but should adopt a posture of “assumed breach." If we are already breached, we assume nothing is clean or can be fully trusted. Therefore, we need to constantly verify, authenticate and authorize all users, devices and network connection through adaptive policies and controls.
Tips for Security Practitioners
Organizations should adopt security-by-design principles and have "secure by default" as the baseline to involve cybersecurity right at the start of any digitalization projects to avoid any surprises. This will ensure that they do not introduce loopholes that malicious actors can leverage.
Applying D.I.E triads, Security Chaos Engineering principles and Zero Trust concepts during the design and solutioning phase and continuously executing them during implementation and operational phase can greatly enhance the security by design and allow security practitioners to really ensure security differently.
CyberEdBoard is ISMG's premier members-only community of senior-most executives and thought leaders in the fields of security, risk, privacy and IT. CyberEdBoard provides executives with a powerful, peer-driven collaborative ecosystem, private meetings and a library of resources to address complex challenges shared by thousands of CISOs and senior security leaders located in 65 different countries worldwide.
Join the Community - CyberEdBoard.io.
Alan Ng is the information security officer at China Taiping Insurance in Singapore. One of his key responsibilities is understanding the current information and cybersecurity posture, the state of MAS TRM compliance and audit findings, past data breaches and key IT-related risks and drafting a strategic plan to bring the company back to tolerance level and meet all regulatory or compliance requirements. In securing and defending against cyberattacks, Ng focuses on people, policy, process and culture combined with the latest technology and best practices.












