DDoS Protection , Events , Fraud Management & Cybercrime
British Cops Bust Suspected German ISP Mirai Botnet Hacker
1 Million Deutsche Telekom Routers Were Disrupted via Mirai Malware
British police arrested a suspected hacker at a London-area airport on Feb. 22 at the request of German police as part of an investigation into the mass hack of Deutsche Telekom customers' routers with Mirai malware.
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
"The NCA arrested a 29-year-old man at Luton airport yesterday morning under a European arrest warrant on behalf of the German police," a spokesman for the National Crime Agency - Britain's national law enforcement and police agency - tells me. "It was in connection with the November 2016 hack on Deutsche Telecom."
The Bundeskriminalamt - the Federal Criminal Police Office of Germany, aka BKA - also announced the arrest in a Feb. 23 press release, saying it was part of an attack investigation involving both the BKA and the prosecutor's office in Cologne.
"The aim of the attack wave was to take over the routers and integrate them into a botnet operated by the accused," the BKA said. "Access to the botnet was allegedly offered by the accused via the darknet for multiple attack scenarios, such as so-called DDoS attacks." If convicted of related charges, the suspect faces between 6 months and 10 years in prison.
The BKA said that beyond the NCA, the EU law enforcement intelligence agency Europol and Eurojust - the EU agency that handles cross-border judicial cooperation relating to criminal matters - were also crucial to its investigation. It said related malware was analyzed by Germany's Federal Office for Information Security, or BSI, and noted that Deutsche Telekom fully cooperated with the investigation.
As noted by Thomas Rid, a professor in security studies at King's College London, the arrest likely relates to launching Mirai botnet attacks.
Reached for comment, a BKA spokeswoman declined to confirm the strain of malware that the suspect allegedly used. "Further information can't currently be provided due to ongoing investigations," she tells me.
NCA arrested suspected "Telekom-Hacker," a Brit, at London airport for "grave computer sabotage," German Federal Police report--likely Mirai pic.twitter.com/e4aMz4RVfs
— Thomas Rid (@RidT) February 23, 2017
Wave of Mirai Malware Attacks
In late November 2016, Deutsche Telekom warned that about 1 million customers had been knocked offline - and telephony and television services also disrupted - after their routers were infected with what security experts said was Mirai malware. The attack triggered an investigation by Germany's National Cyber Defense Center (see Mirai Botnet Knocks Out Deutsche Telekom Routers).
Mirai malware is designed to target default accounts and passwords in dozens of different types of internet-connected devices, including digital video recorders, routers, baby monitors and CCTVs. At last week's RSA Conference in San Francisco, numerous information security experts said the low cost of so many internet-connected devices had led to device security being an afterthought - if the devices were secured at all.
Mirai malware was tied to a record-setting Oct. 21 distributed denial-of-service attack against domain name service provider Dyn - which peaked at a reported 1.1 Tbps - as well as another massive DDoS attack against the website of information security blogger Brian Krebs (see Free Source Code Hacks IoT Devices to Build DDoS Army).
Life After Poodlecorp
Mirai was originally controlled by an individual or group calling itself Poodlecorp.
What's not clear now, however, is how many different cybercrime groups or individuals now run Mirai botnets.
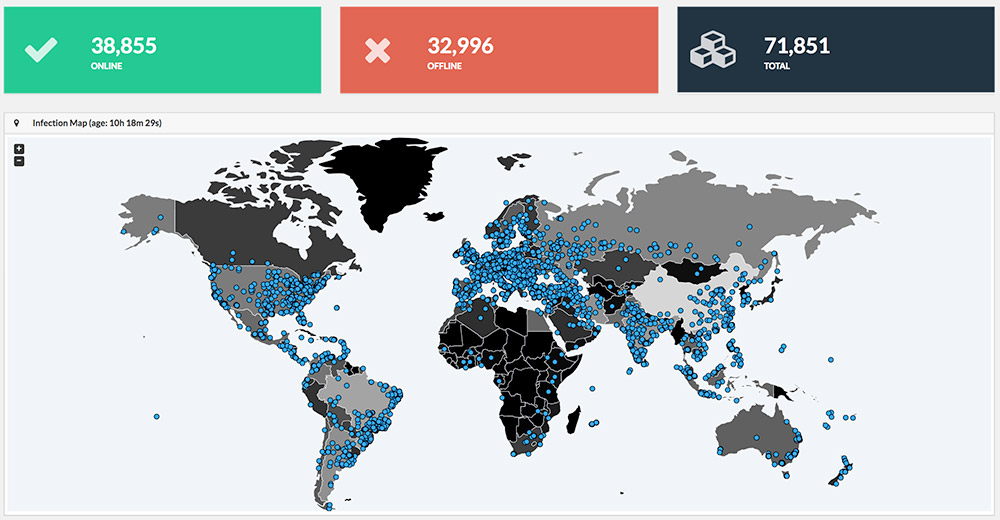
"Mirai was once [controlled] by PoodleCorp and they even stated they would attack on the 21st [of October 2016], specifically EA's Battlefield 1 launch day," Bryant Townsend, CEO of DDoS defense firm BackConnect, has told me.
Subsequently, however, someone calling themselves "Anna-senpai" publicly released the source code for Mirai, thus allowing any would-be attacker to roll their own Mirai botnet, "which now makes it difficult to attribute the attack to any individual or organization," according to Townsend.
"One person writes the Mirai botnet and then publishes its code, and then within a week it's in dozens of botnets," security expert Bruce Schneier, CTO of IBM's Resilient, said at last week's RSA conference. "That's our world."
Who Throws Away Old Routers?
Security experts say that too many internet-connected devices continue to be built with poor or absent security controls. Many device manufacturers have also failed to ensure that they can remotely push patches to vulnerable devices or otherwise get them into users' hands.
As a result, there are hundreds of thousands - if not millions - of internet-connected devices that could be remotely exploited by attackers to serve as launch pads for further attacks. The devices can also be used in tandem to launch massive DDoS attacks, as was seen in the Dyn disruption.
The best fix for a poorly secured IoT device has long been to throw it away and buy a new one, according to information security consultant Brian Honan, who's a Europol cybersecurity adviser.
Unfortunately, that isn't working. As a result, some security experts have called for such devices to be regulated. "The market is not going to fix this, because neither the buyer or the seller care," Schneier said.
Tough love may be the only solution. "The government should definitely do something about it - they should not allow devices which are not sufficiently secure to be connected to the public internet," cryptographer Adi Shamir - the "S" in the RSA cryptosystem - said at the RSA conference.
Additional Summit Insight:
Hear from more industry influencers, earn CPE credits, and network with leaders of technology at our global events. Learn more at our Fraud & Breach Prevention Events site.











