Data Loss Prevention (DLP) , Encryption & Key Management , Governance & Risk Management
Attack Alert: JavaScript Spam Installs Ransomware
Beware JavaScript Social Engineering Emails, Microsoft Warns
Warning: A recent spate of spam emails has been tricking users into installing several different JavaScript-based downloaders, which then install well-known ransomware that's designed to forcibly encrypt all files on a PC, Microsoft warns (see FBI Warning: Ransomware Is Surging).
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
"Be wary of emails with JavaScript attachments," says Alden Pornasdoro, who's part of Microsoft's malware protection group, in a blog post. "It is uncommon and quite suspicious for people to send legitimate applications in pure JavaScript file format - files with .js or .jse extension - via email. Do not click or open it."
Microsoft hasn't detailed how many users might have fallen victim to these social engineering attacks. But it warns that it's seen a surge in three different types of malicious downloaders written in JavaScript - Locky, Nemucod and Swabfex - being installed on PCs, and used to then download and install ransomware.
"Just like a typical email campaign, the JavaScript-toting spam finds its way [onto] your PC after a successful social engineering trick," Pornasdoro says. Said trickery often involves attackers picking interesting-sounding names, for example related to purported financial documents. First, however, users have to fall for the ruse by expanding a .zip or .rar file attached to the email, inside which is the malicious JavaScript, which they must then click to execute.
Spam Leads to Locky, TeslaCrypt
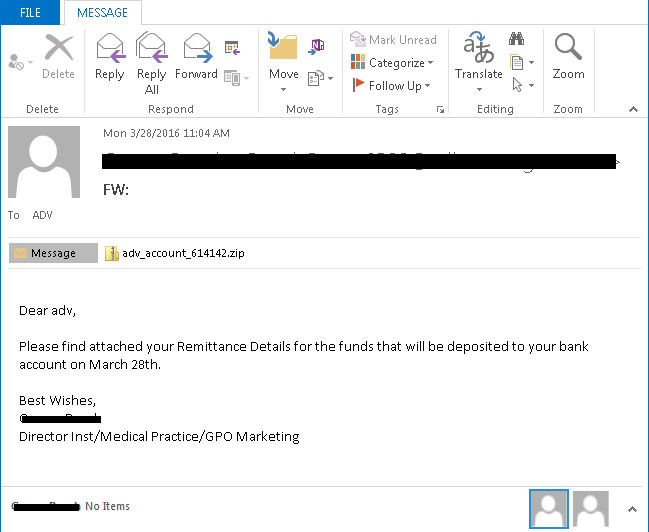
With this particular JavaScript campaign, Microsoft says attackers have been using the downloaders to install two types of ransomware:
- Tescrypt: Also known as TeslaCrypt and Bitman, this ransomware often gets dropped by such exploit kits as Angler, Fiesta, Nuclear, and Sweet Orange, some of which may now be responsible for the JavaScript spam attacks.
- Locky: This ransomware has been tied to many recent attacks, most notably against hospitals.
Ransomware Gets Commoditized
But like banking Trojans, much of the ransomware being used by attackers today is functionally equivalent: It will forcibly encrypt sensitive files on a PC, then demand a ransom payment - in bitcoins - in exchange for a decryption key. Then it's up to organizations or end users to either wipe the infected system and restore a recent backup, or else to decide if they're going to pay the ransom (see Ransomware: Is It Ever OK to Pay?).
While anti-virus software should theoretically be able to block ransomware from being installed, by employing JavaScript, attackers have been evading many such defenses. "The JavaScript attachments are heavily obfuscated to avoid anti-virus software detections. It consists of a download and execute function paired with one or two URLs hosting the malware," Pornasdoro says.
As is typical with many types of malware or ransomware campaigns, attackers will then quickly discard the URLs and move to new ones, so that by the time security firms blacklist the URL - so that future, infected endpoints can't "phone home" to it - the URL is no longer in use.
Defending Against JavaScript Spam
To guard against these types of attacks, Microsoft recommends employing related defenses at the following levels:
- Gateway: Ensure email gateways are scanning for malicious code and blocking it there.
- Endpoint: Use up-to-date and fully patched anti-malware and anti-spyware software.
- Macros: Disable macros in Office programs, and set Group Policy settings to disable macro loading.
- Training: Educate users to never click or open email attachments that carry files with .js or .jse.
Bad Bet: Crypto Coding Failures
In some cases, for example earlier this month with Petya ransomware, or last year with a previous version of TeslaCrypt, ransomware developers make coding mistakes that allow researchers to crack their crypto and release a free decryption tool.
Attackers fumbling their ransomware crypto is a "lucky break" for anyone whose systems were infected, says Johannes Ullrich, CTO of the Internet Storm Center, in a recent SANS Institute newsletter. But there's never a guarantee that ransomware coders will screw up, and it's a sure bet that when they do, the next iteration of their ransomware will avoid making the same mistake.
"Remember that the real defense against crypto ransomware is offline backups - which also helps against a number of other disasters," Ullrich says.











