COVID-19 , Governance & Risk Management , Identity Governance & Administration
Why Are We So Stupid About RDP Passwords?
Ransomware Gangs Keep Pwning Poorly Secured Remote Desktop Protocol Endpoints
In honor of World Password Day, here's a task for every organization that uses remote desktop protocol: Ensure that all of your organization's internet-facing RDP ports have a password - and that it's complex and unique (see: Party Like Every Day Is World Password Day).
See Also: The Cybersecurity Swiss Army Knife for Info Guardians: ISO/IEC 27001
Even better: Ensure that RDP access is only allowed via VPN, requires multifactor authentication to access, and that network-level authentication is enabled, which requires that anyone attempting to connect to a system via RDP first authenticate before they're allowed to establish a session.
While this might seem like no-brainer advice, numerous security watchers have been charting an increase in attackers pummeling poorly secured RDP endpoints. And with COVID-19 stay-at-home measures driving a surge in remote working, the number of RDP endpoints in use appears to also have been increasing, thus giving attackers more potential targets from which to choose (see: Is COVID-19 Driving a Surge in Unsafe Remote Connectivity?).
"The number of RDP ports exposed to the internet has grown quickly, from roughly 3 million in January to more than 4.5 million in March," reports security firm McAfee, based on research conducted with internet of things search engine Shodan. It found that far and away the biggest number of RDP ports are being exposed in China - where there were 200,000 - and the United States.
There's been some debate about whether there are now more internet-exposed RDP endpoints than normal. In late March, for example, responding to figures published by Shodan, both IoT search engine BinaryEdge and Boston-based security firm Rapid7 told me that while they'd seen fluctuations in the total number of RDP endpoints, they appeared to still be within normal tolerances.
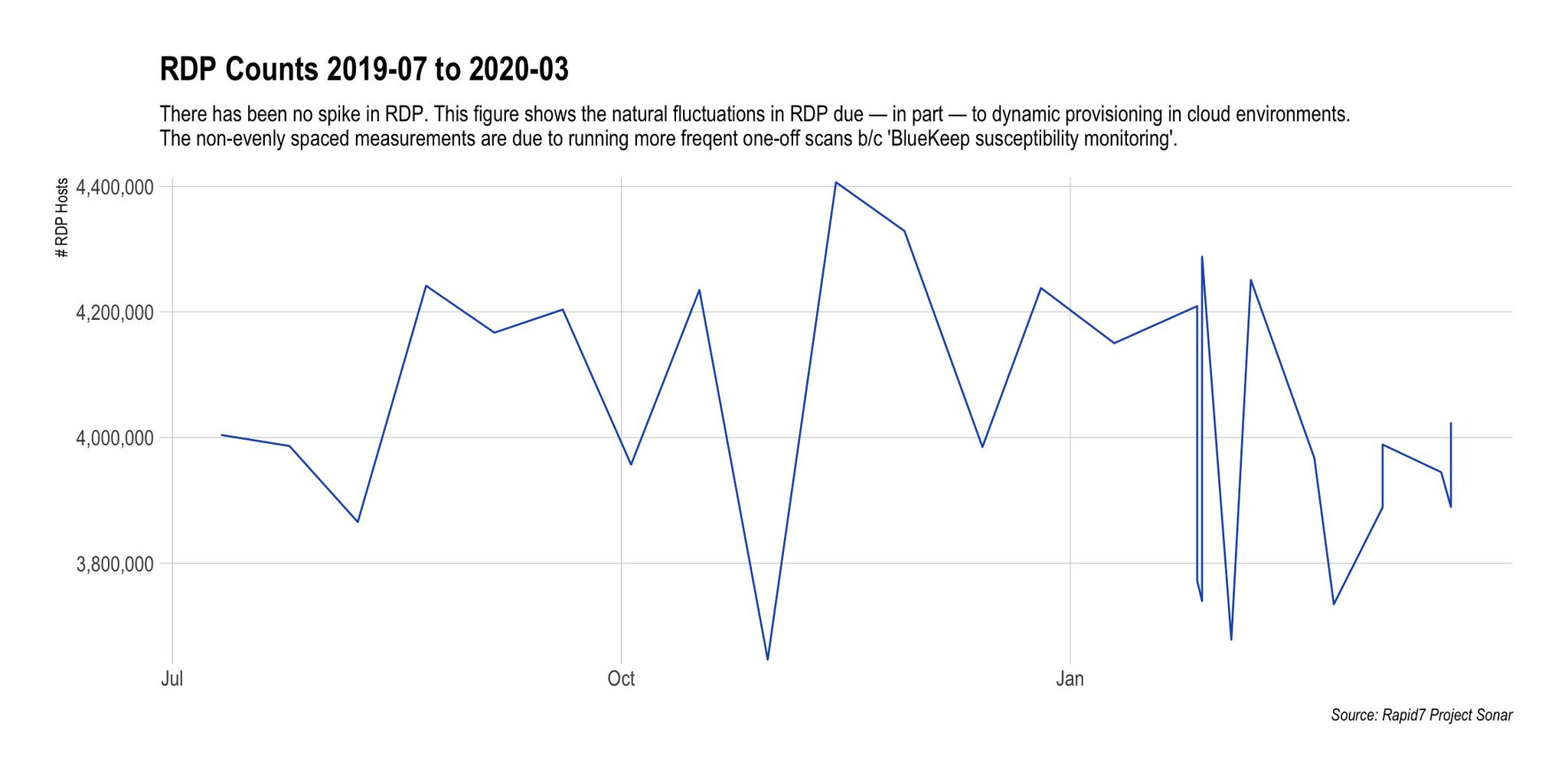
Tiago Henriques, CEO of Zurich-based BinaryEdge, says that as of this week, RDP usage appears to still be typical.
"We continue to see RDP endpoints stable at 4.4 million to 4.6 million, as we have for more than 6 months," he tells me. "In terms of exposure it is exactly the same, but we do see on our sensors a higher number of attacks."
Increasing: Attacks Against RDP Ports
Likewise, McAfee also reports that it's been tracking "an increase in both the number of attacks against RDP ports and in the volume of RDP credentials sold on underground markets."
Hackers are continuing to pummel RDP endpoints because if they can be accessed, they gain an easy way to gain remote access to a network. From there, they can steal data and install any type of malware they want, including ransomware (see: Ransomware Gangs' Not-So-Secret Attack Vector: RDP Exploits).
Law enforcement agencies continue to target and shutter some of the cybercrime forums and marketplaces that sell stolen or brute-forced RDP credentials, which have at times sold for as little as $3, although $20 appears to be closer to today's going rate.
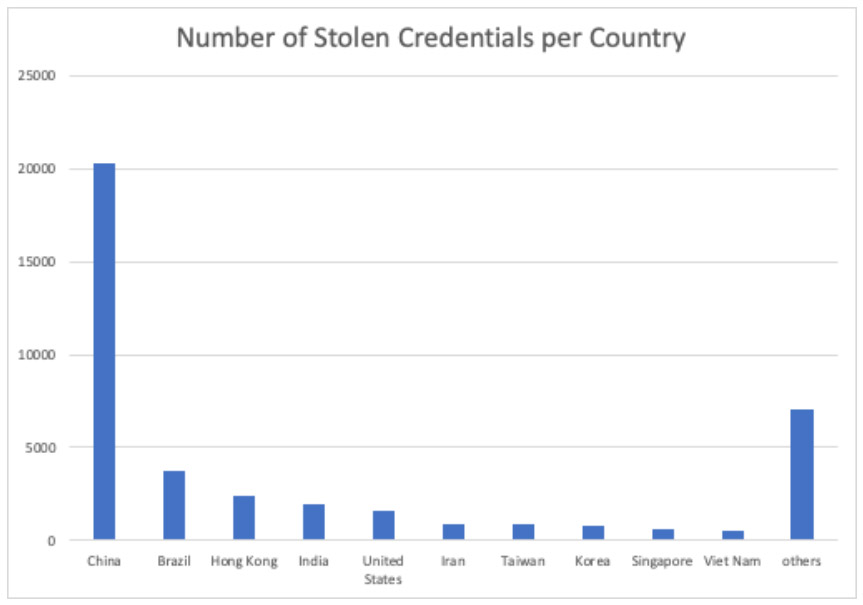
Cybercrime may have the aura of wunderkind hackers magically penetrating corporate networks with Fort Knox-level defenses. In fact, the way attackers operate online is often very banal. "The way they're getting into organizations isn't necessarily remarkable, it's things like this, where you've got the sale of credentials online," Raj Samani, chief scientist at McAfee, tells me.
Widespread: Poor RDP Passwords
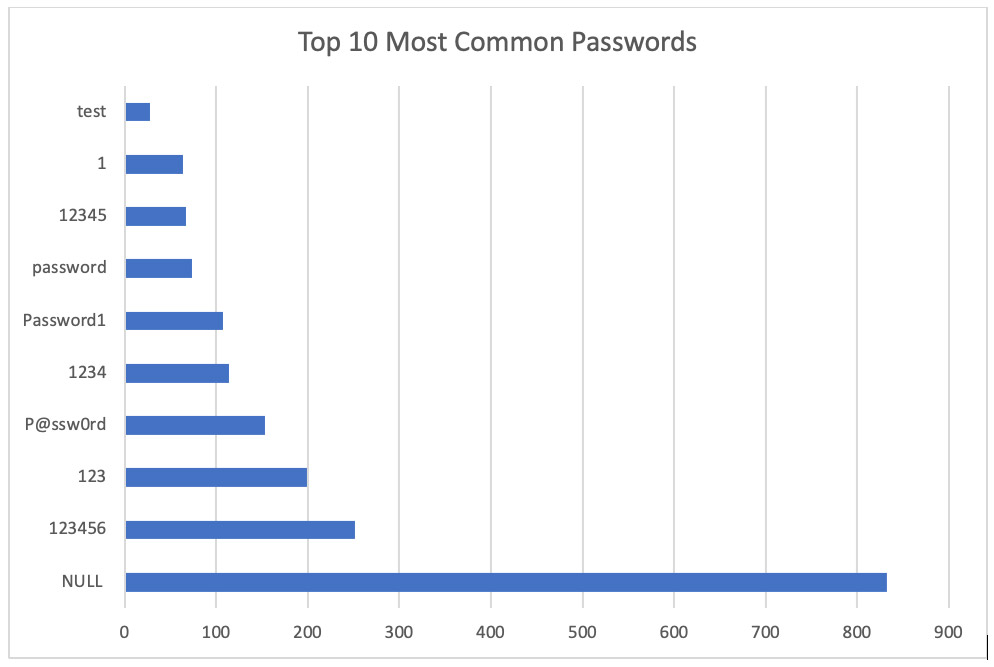
Reviewing data shared by an unnamed law enforcement agency that had disrupted RDP shops, McAfee found that many of the RDP credentials for sale featured appallingly bad passwords.
Far and away the most common was "null," meaning there simply wasn't a password. Some of the other 10 most common approaches were using "123456" and "P@ssw0rd," not to mention "password" and "test." Such passwords are child's play for attackers with dictionary lists to crack (see: Why Are We So Stupid About Allowing Overused Passwords?).
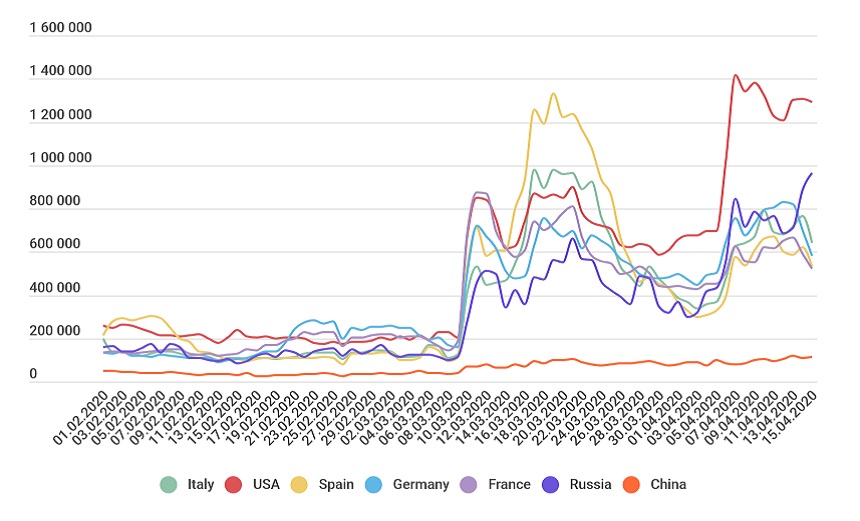
Security firm Kaspersky, based in Moscow, reports seeing a massive spike in brute-force attacks against RDP endpoints since work-from-home rules went into effect. From February to April, it saw the volume of such attacks more than triple (see: RDP Brute-Force Attacks Rise During COVID-19 Crisis: Report).
Ransomware Gangs Love RDP
Gaining remote access to corporate networks - for example, via brute-forced or stolen RDP credentials - can be used by any hacker, but some ransomware gangs, in particular, are big fans of the technique.
In a recent report, Microsoft calls out attackers wielding four strains of ransomware - RobbinHood, Vatet loader, Maze and RagnarLocker - as being regular users of stolen or brute-forced RDP credentials (see: 10 Ransomware Strains Being Used in Advanced Attacks).
So long as buying cheap RDP credentials works for gaining remote access to networks, attackers will continue to do so. The ease, affordability and reliability of these tactics helps explain how ransomware gangs are continuing to turn such large profits (see: Ransomware: Average Business Payout Surges to $111,605).
"The reality is the majority of these attacks are exploiting very, very common vulnerabilities within corporate networks," Samani says. "It's very simple: People have open RDP ports; people don't have security on the RDP ports."
Beyond that, what should organizations be doing better? For starters, don't use weak passwords. Also have defenses in place in case attackers do gain access, especially to combat ransomware. "Make sure you're monitoring what goes on in your environment, and make sure that you've got backups that are not online and which are disconnected from your organization - offline backups," Samani says.
How to Secure RDP Access?
Here are McAfee's top tips for ensuring RDP endpoints don't become a security liability:
- Do not allow RDP connections over the open internet.
- Use complex passwords as well as multifactor authentication.
- Lock out users and block or timeout IPs that have too many failed logon attempts.
- Use an RDP gateway.
- Limit Domain Admin account access.
- Minimize the number of local admins.
- Use a firewall to restrict access.
- Enable restricted Admin mode.
- Enable network level authentication, or NLA.
- Ensure that local administrator accounts are unique and restrict the users who can logon using RDP.
- Consider placement within the network.
- Consider using an account-naming convention that does not reveal organizational information.
Security researchers have been warning for some time that organizations with remote services enabled must ensure they're protected against BlueKeep, a vulnerability that was first disclosed by Microsoft in May 2019, when it released a patch. Designated CVE-2019-0708, the vulnerability, which exists in many versions of Windows' remote desktop services, can allow an attacker to gain authentication-free access to a machine via RDP by using specially crafted requests.
By applying the above, organizations can ensure that RDP is only being tapped by approved users. Because leaving it easily accessible to hackers simply wouldn't be smart.











