Forensics , Fraud Management & Cybercrime , Governance & Risk Management
Accellion Attack Involved Extensive Reverse Engineering
Sophisticated Attackers Took the Time to Master a 20-Year-Old Product, FireEye Says
Using a nearly 20-year-old file transfer product - what could go wrong?
See Also: The Cybersecurity Swiss Army Knife for Info Guardians
Among the many lessons to be learned from the Accellion File Transfer Appliance mess is this: Attackers will devote substantial resources to reverse-engineer hardware, software or a service if they see a financial upside.
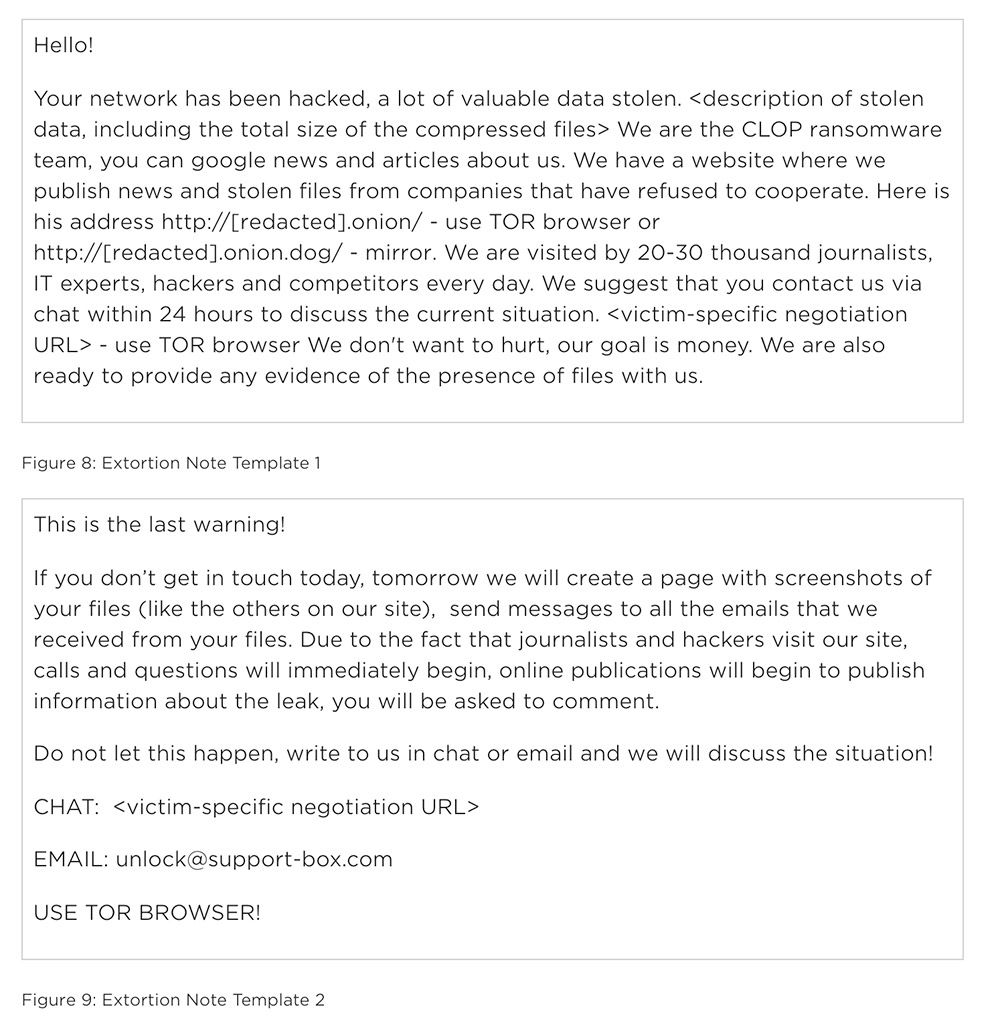
In the case of Accellion's FTA, reverse engineering enabled attackers to drop a web shell - a script that enables remote execution of commands - onto any server running the FTA software, according to FireEye's Mandiant incident response group, which Accellion hired to investigate. The web shell allowed attackers to bypass authentication, remotely execute code on the vulnerable systems and steal data. In at least some cases, stolen data ended up in the hands of the Clop ransomware gang, which has been offering to sell it or to remove it if victims pay a ransom (see: Accellion: How Attackers Stole Data and Ransomed Companies).
Luckily, the attack came to light relatively quickly after attackers inadvertently began triggering error messages for customers, according to Mandiant.
In a final report into the Accellion breach issued Monday, Mandiant says attackers exploited two zero-day flaws in a December 2020 attack and two different zero-day flaws in a January attack.
The attacks - and research required to find the zero-day flaws - "demonstrate a high level of sophistication and deep familiarity with the inner workings of the Accellion FTA software, likely obtained through extensive reverse-engineering of the software," Mandiant reports.
The investigators say attackers identified:
- How to call internal APIs to obtain keys to decrypt filenames;
- How to forge tokens for internal API calls;
- How to chain together the vulnerabilities involved to conduct unauthenticated remote code execution;
- How to navigate FTA’s internal database, requiring a detailed understanding of the database structure;
- How to bypass FTA’s built-in anomaly detector (in the case of the January exploit).
In the first attack campaign starting last December, using a previously unknown SQL injection flaw - CVE-2021-27101 - attackers planted a web shell - named "Dewmode" by Mandiant - on vulnerable systems. The web shell includes the ability to delete FTA logs to help attackers hide their tracks.
But attackers' knowledge of FTA didn't appear to be complete. "The uploading of the Dewmode web shell to the file location where the attacker placed it had the effect (likely unanticipated by and unknown to the attacker) of tripping the built-in anomaly detector included in the FTA software," Mandiant reports. "Once the anomaly detector is tripped, it generates an email alert to the customer (specifically to the admin email account designated by the customer), advising the customer to contact Accellion for support. As a result, any FTA customer affected by the December exploit likely was sent such an email - which, per Accellion, is how the December exploit came to its attention."
By Jan. 20, attackers had retooled, following Accellion patching the first two zero-day flaws. "Notably, in the case of this second exploit, the attacker uploaded the Dewmode web shell to a different location (/home/httpd/html/about.html), likely to avoid FTA’s built-in anomaly detector," Mandiant says. "The earliest evidence we have seen of this change in tactic appears on January 20."
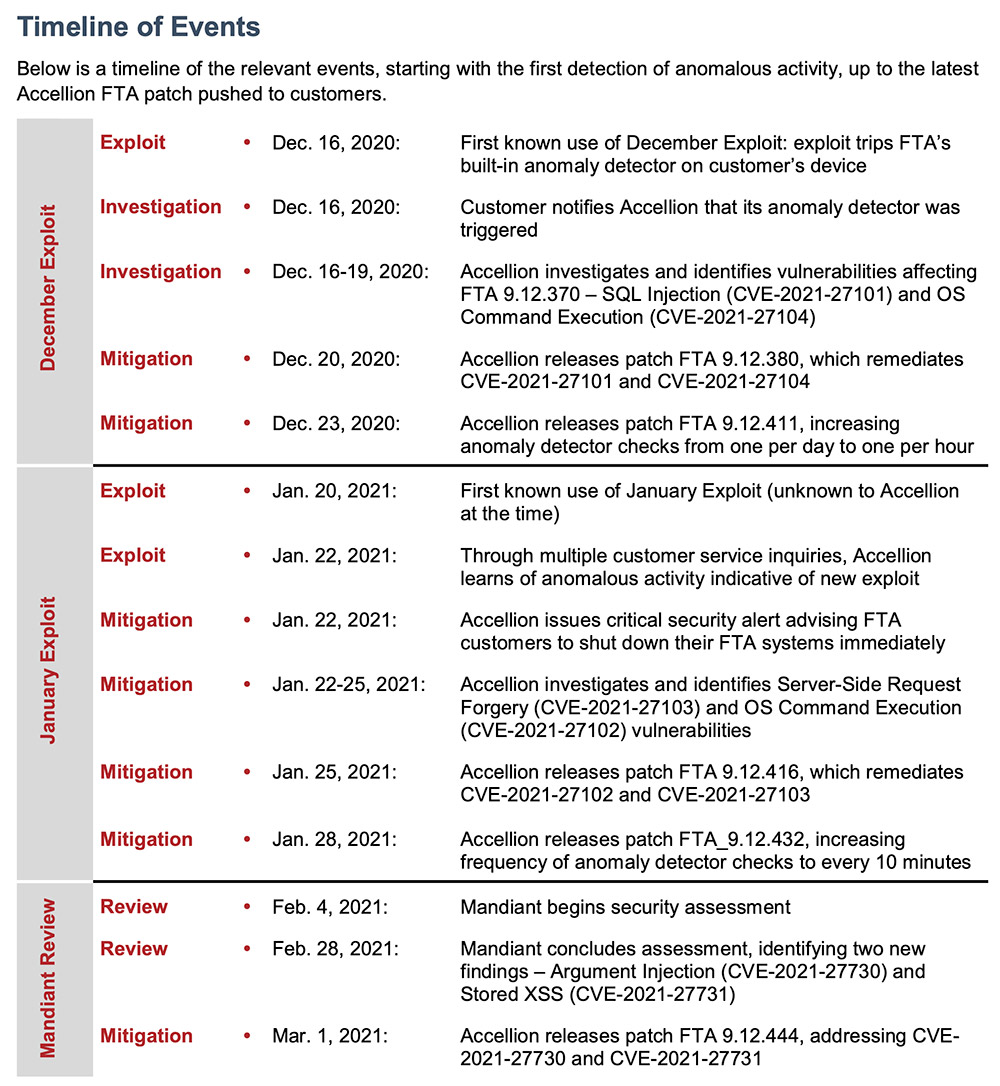
Mandiant says it has validated that all FTA patches issued by Accellion have fully blocked the attacks. In addition, it has reviewed FTA for signs of any further vulnerabilities, using both source code analysis and dynamic penetration testing, and found two further vulnerabilities that could be exploited by authenticated users. The flaws - an argument injection available to users with administrative-level access and a cross-site scripting attack - have been patched by Accellion with the release of FTA version 9.12.444, which Mandiant says it has also tested.
The Quest for Ransomware Profits
Who would go through all of this effort? The answer appears to be individuals associated with the Clop ransomware operation.
Developing a novel exploit for a widely used piece of software makes sense, if you're a criminal, because the investment has the potential to produce massive returns.
Confirmed victims of this attack campaign include the Reserve Bank of New Zealand, and in Australia, securities regulator ASIC, government agency Transport for New South Wales and QIMR Berghofer Medical Research Institute. Other victims include Canadian aerospace firm Bombardier, the Office of the Washington State Auditor; the University of Colorado and U.S. grocery chain Kroger.
Since last week, Clop's data leak site has also claimed fresh victims, including U.S. railway freight-hauling giant CSX, Toronto-based testing and certification organization CSA Group, Paris-based geoscience technology firm CGG and Ohio-based medical equipment manufacturer Steris. It's not clear if all of those firms are FTA users.
And cybersecurity firm Qualys is likely the latest victim, Bleeping Computer reported Wednesday.
Especially for ransomware gangs, hitting large organizations - via what's known as big game hunting - helps maximize the profit from any given attack. Running more such attacks helps increase the number of those willing to pay a ransom. Cue a rise in profits.
Imperative: Migrate to New Software
For organizations that continue to use FTA, it's time to move on.
Accellion says it will stop supporting FTA on April 30. It notes that for three years, it's been urging remaining users to ditch "legacy FTA software" and migrate to its newer product, Kiteworks, which is based on an entirely different code base. The company says Kiteworks is more secure.
Any organization continuing to use FTA is on borrowed time and should ensure it is fully patched as well as backed by rigorous log collection and analysis, and access review, Drew Schmitt, a senior threat intelligence analyst with GuidePoint Security in Herndon, Virginia, says in a guide for remaining FTA users.
Given the risk posed by the legacy software, he says that the imperative for users is clear: "Let’s move off this platform as soon as possible."
In the bigger picture, that should be the mantra for any organization that continues to use legacy software: Is it worth the risk? As a number of FTA users will now tell you, get that answer wrong, and you might face serious consequences.













