Critical Infrastructure Security , Cybercrime , Cybercrime as-a-service
BlackMatter Ransomware Claims to Be Best of REvil, DarkSide
Also, Repurposed REvil Code Used to Infect New Victim - Likely by Former Affiliate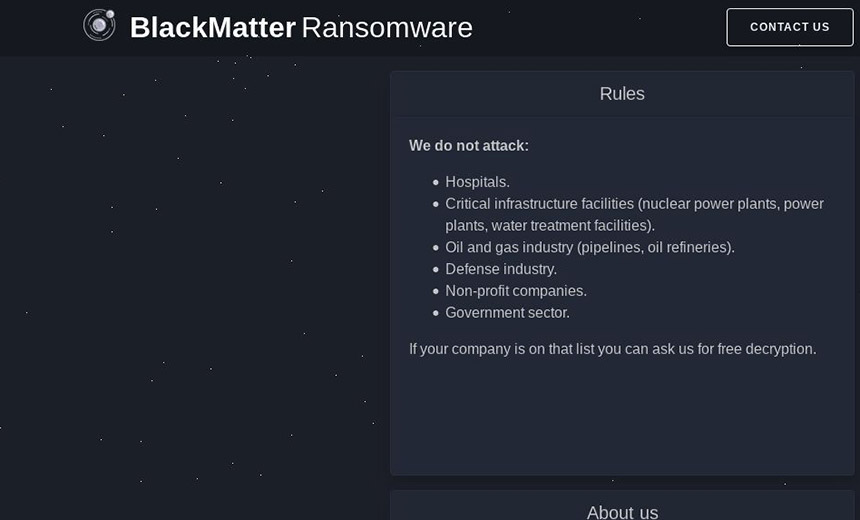
Update (July 29): This story has been updated to clarify that there is no evidence that the REvil reuse spotted by Wosar is connected to the emergence of BlackMatter.
See Also: The State of Organizations' Security Posture as of Q1 2018
Has a new group emerged from the ashes of the apparently now defunct REvil or DarkSide ransomware groups?
Threat intelligence firms say that earlier this month, a previously unknown user with the handle "BlackMatter" announced the launch of BlackMatter Ransomware via two large, Russian-language forums, saying it offered a "greatest hits" take on some of the most notorious ransomware operations in history.
"The project has incorporated in itself the best features of DarkSide, REvil and LockBit," BlackMatter claimed in July 19 posts, says threat-intelligence firm Recorded Future.
The choice of name for the ransomware group recalls REvil. "REvil previously labeled their Windows Registry key 'BlackLivesMatter,'" says threat intelligence firm Flashpoint.
That key name was present in the version of REvil used in the attack against the software firm Kaseya, says Kevin Beaumont, head of the security operations center for London-based fashion retail giant Arcadia Group.
Has REvil Disbanded?
The emergence of BlackMatter follows REvil apparently shutting down following the July 2 attack it unleashed via Kaseya's remote management software, infecting about 60 of its managed service provider customers and up to 1,500 of their clients' systems. On Thursday, Kaseya said it had obtained the ability to decrypt every victim's files and was helping them do so, and on Monday it issued a statement clarifying that it had not paid a ransom to REvil for a decryptor.
On July 13, REvil apparently shut down its data leak site and payment portal. "On the same day, XSS banned REvil's spokesperson UNKN" - aka Unknown - Flashpoint says, referring to the XSS darknet criminal forum.
Whether REvil has shut down operations and potentially decided to rebrand and begin again under a different name - or might do so - remains unclear. "We have certainly noticed that they've stood down their operations. We don't know exactly why," a White House official told Politico last week.
Fresh Attack Using REvil Code
At least one organization has fallen victim to a new attack involving REvil's code, says Fabian Wosar, CTO at Emsisoft. "REvil is back … at least sort of. We have seen a victim that was clearly hit by a patched REvil variant. The attacker likely patched an existing REvil payload to leave out the key blob that is usually encrypted, with the operator blob nulling it out," Wosar says via Twitter.
Wosar says whoever is wielding REvil may be one or more former affiliates of one or more ransomware-as-a-service operations. In such operations, administrators develop crypto-locking malware, which affiliates access as a cloud-based service, via a portal. Affiliates use the code to infect organizations, and whenever a victim pays a ransom, the affiliate and the operation's administrators share in the profits.
But in terms of REvil, Wosar says the attacker is likely not "OG" - slang for original gangster, referring in this case to being a core member of the original crew. "We do not believe this to be the work of the OG REvil operators or someone who had access to the REvil source code," he says. "It is more likely we are dealing with a former affiliate here who doesn't want to accept that his favorite ransomware operator went dark. Gotta pay rent somehow."
And while we are at it: REvil is back as well. At least sort of. We have seen a victim that was clearly hit by a patched REvil variant. The attacker likely patched an existing REvil payload to leave out the key blob that is usually encrypted with the operator blob nulling it out. pic.twitter.com/fnLgCmboQM— Fabian Wosar (@fwosar) July 27, 2021
New Operation Advertises
Whoever is behind BlackMatter, meanwhile, appears set to expand. The "BlackMatter" user account was first registered on July 19 on the XSS and Exploit criminal forums, where it advertised for help, Flashpoint says.
Recorded Future notes that the group also created an escrow account with Exploit, depositing 4 bitcoins, worth about $120,000.
Escrow accounts are used by forums to protect buyers and sellers. For example, if a seller provides a service and a buyer fails to pay, the seller can file a complaint with the forum. If it's upheld, the forum can debit the amount from the buyer's escrow account to compensate the seller.
The relatively large amount put into the escrow account by BlackMatter shows the group is serious, Flashpoint says. But much remains unknown. "Two posts and a large escrow account do not make a ransomware group," it says. "It is possible that copycats are intentionally mimicking the behavior of REvil to gain immediate credibility for allegedly being the reincarnation of REvil."
On July 21, meanwhile, BlackMatter "posted a notice on the forums, stating they are looking to purchase access to infected corporate networks in the U.S., Canada, Australia, and the U.K." with more than $100 million in annual revenue, "presumably for ransomware operations," Flashpoint says.
On BlackMatter's dedicated data leak site, the group claims to not hit hospitals, organizations that operate critical infrastructure, defense contractors or government agencies, among other types of targets.
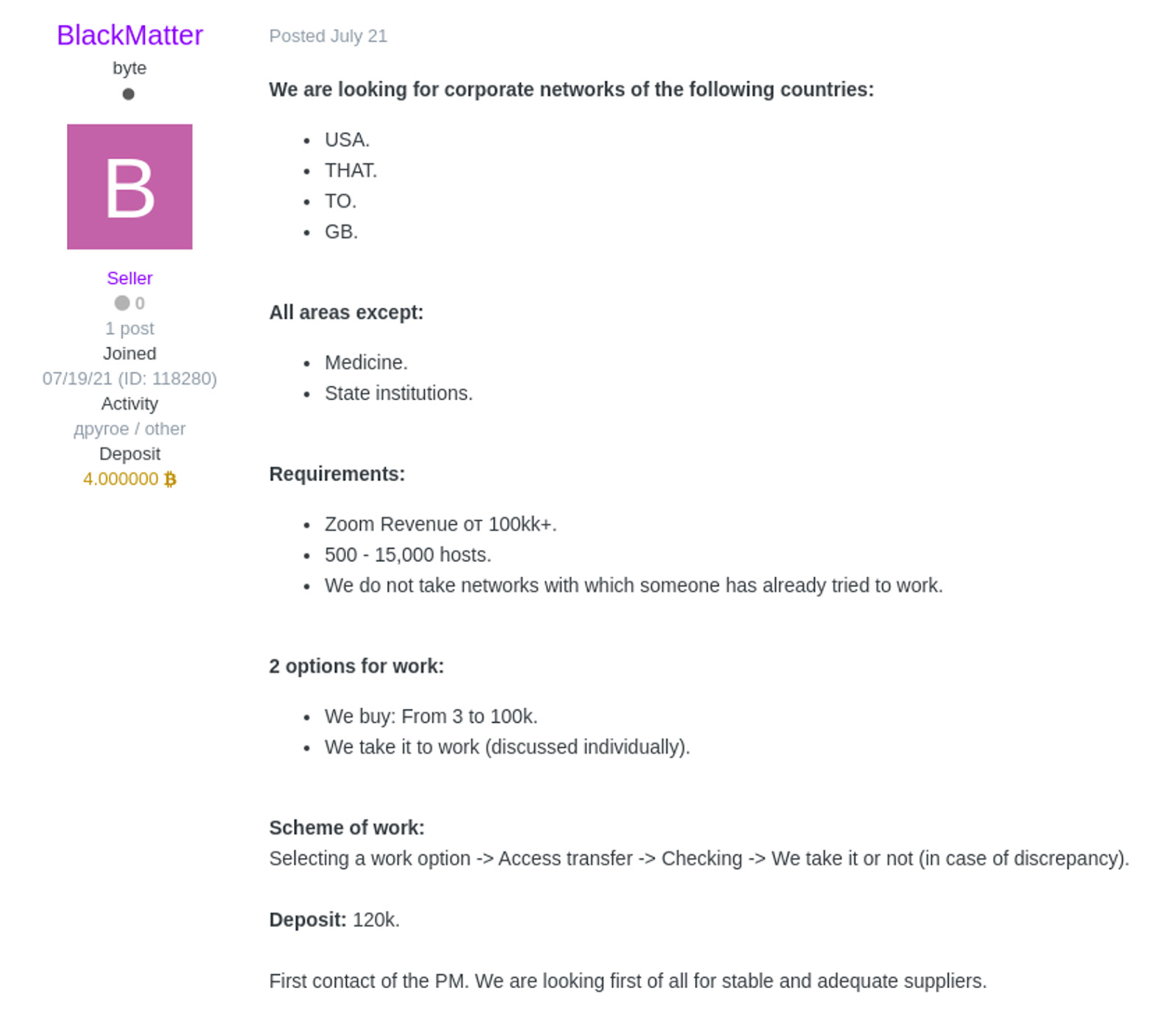
BlackMatter has been offering initial access brokers the choice of a one-off payment of $3,000 to $100,000 or a share of any ransom a resulting victim might pay, Recorded Future notes.
"They have implemented requirements for these partners, likely to filter out security researchers and law enforcement, especially now given the significant media attention," says Kimberly Goody, director of financial crime analysis for FireEye's Mandiant threat intelligence division. "Examples of these requirements include having an older profile on the forum with a minimum number of posts, providing proof of previous work with another ransomware, or providing confirmation of accesses to at least two large companies with revenues over $100 million."
Forums Have 'Banned' Ransomware
Security experts say BlackMatter and other groups appear to be getting around the forums' bans on ransomware in their attempt to recruit people to work with them.
Those bans have been in effect on at least some of the biggest Russian-speaking cybercrime forums - Exploit, Raid and XSS - following two attacks in May: DarkSide hitting Colonial Pipeline Co. and Conti hitting Ireland's health service.
"No matter how patriotic you are as a hacker or how little you care about being arrested, when you get to that level of scrutiny, nobody wants that on them, "says Bob McArdle, director of cybercrime research at security firm Trend Micro. "So there is definitely a push in the forums that - at least for now - for the time being, this is a topic that you cannot talk about."
Big operators likely already have established relationships and don't rely heavily on forums for recruiting new business partners. But that hasn't stopped other forum users from still appearing to advertise or recruit for help for their ransomware operations in the form of affiliates and others, only "they're trying to be slightly clever about it," McArdle says. For example, forum users will advertise looking for access brokers or "pentesters" - aka penetration testers - "who can get into large networks and deploy our product," he says.
Criminals also find other ways to advertise. The AvosLocker ransomware operation on Thursday used a service for distributing spam via Jabber and Telegraph to advertise its ransomware partner program, Flashpoint reports (see: AvosLocker Ransomware Gang Recruiting Affiliates, Partners).
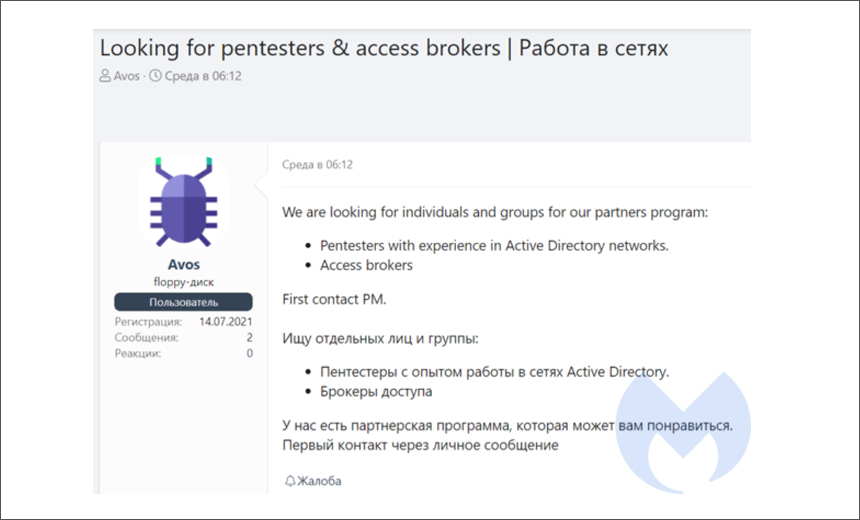
"Prior to that, ransomware actors have also maintained communications on a number of other platforms. Some, such as Black Shadow, maintain Telegram accounts, others, such as LockBit 2.0, run ransomware-as-a-service recruitment on their forums, and still others have moved to new forums for RaaS recruitment such as Babuk's RAMP forum," it says.





















