Cybercrime , Cybercrime as-a-service , Endpoint Security
Black Basta Claims Responsibility for AGCO Attack
AGCO Confirms Staff Data Stolen by Ransomware Gang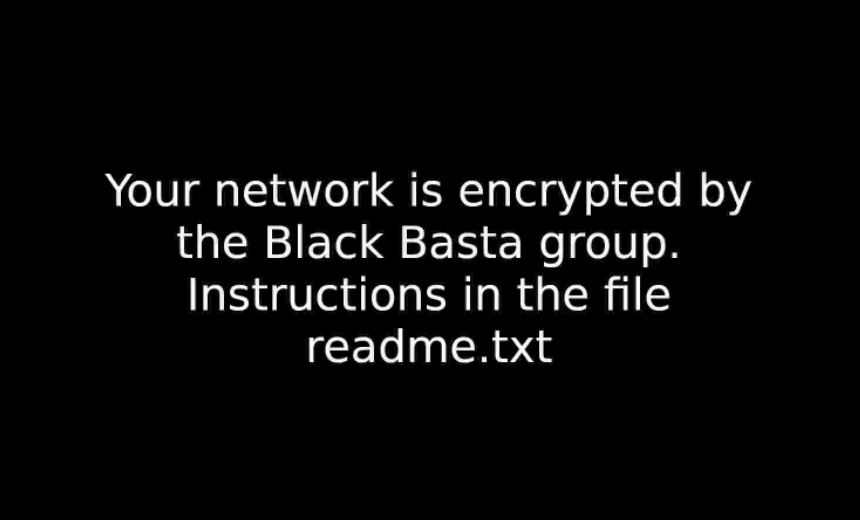
Ransomware gang Black Basta has claimed responsibility for an online attack against agricultural equipment manufacturing and distribution company AGCO Corp. The threat actor, which came to prominence in April, listed the U.S. company's name on its leak site on Wednesday.
See Also: Modernizing Malware Security with Cloud Sandboxing in the Public Sector
AGCO was attacked on May 5, 2022.
#BlackBasta claims responsibility for the #cyberattack against #AGCO, a US manufacturer and distributor of agricultural equipment. #AGCO is publicly-traded under the symbol "AGCO" on the NYSE. The data published by #BlackBlasta so far contains PII.#ransomware #databreach #GDPR pic.twitter.com/JCyi9gnlCz
— BetterCyber (@_bettercyber_) May 25, 2022
Black Basta operators also posted a sample of the allegedly exfiltrated data on the group's leak site, as seen in the redacted tweet above.
An AGCO spokesperson confirmed to Information Security Media Group that employee data had been exfiltrated during the ransomware attack, but declined to comment on whether Black Basta was behind the attack or on the veracity of the exfiltrated data on the threat group's website.
"Data exfiltration has occurred as part of the May 5 cyber ransomware attack. We have notified employees that the recent cyber ransomware attack may have impacted their personally identifiable information. We are arranging identity protection services for all employees to help reduce the concern and impact this incident may cause," the AGCO spokesperson says.
"We are working closely with the appropriate law enforcement agencies and relevant data privacy authorities in various countries," the spokesperson adds.
Attack Summary
On May 5, AGCO announced that it had been the subject of a ransomware attack that affected some of its production facilities. At the time, AGCO stated that the extent of the attack was being investigated, but that it "anticipated its business operations will be adversely affected for several days and potentially longer to fully resume all services depending upon how quickly the company is able to repair its systems."
On May 16, in an updated statement, AGCO said that a majority of the affected production sites and operations had resumed activities within a week. The rest were expected to resume by May 22, restoring full operations.
The AGCO spokesperson tells ISMG that "most of our facilities have resumed production, enabling AGCO to continue serving the world's farmers. Protecting our systems and data against any further threat as well as completing ongoing recovery efforts from the May 5 attack are our priorities."
In the updated statement, AGCO confirms that no consumer data was affected as the "company does not have retail operations." Therefore, "no privacy-protected consumer data [was impacted]. [However], the company is still evaluating the scope and consequences of the data loss," the statement says.
To make up for production loss during downtime resulting from the ransomware attack, AGCO plans to increase production over the remainder of 2022.
Black Basta: Newcomer or Conti Rebrand?
In April, a ransomware group called Black Basta caught the attention of cybersecurity experts when it claimed to have hit the American Dental Association (see: American Dental Association Hit by Disruptive Cyber Incident).
Around the same time, Black Basta listed 10 other victims on its data leak site, reported Israeli threat intelligence firm Kela.
Brett Callow, a threat analyst at security firm Emsisoft, at the time told ISMG, "Black Basta is a new operation that seems to be picking up pace. The ransomware appears to be unrelated to other strains and, unfortunately, is secure - meaning that the only ways to recover encrypted data are by replacing it from backups or by paying the ransom."
But the MalwareHunterTeam had a different opinion. In a tweet, the team said it had noted many similarities between the Black Basta leak site, payment site, negotiation style and support channels and those of Conti, raising speculation that the group was a spinoff of the Russia-linked threat actor.
Black Basta's Modus Operandi
Trend Micro, a cybersecurity solutions provider, details Black Basta's modus operandi in a recent report.
On April 20, Trend Micro first noticed a user named Black Basta on underground forums, who was asking to buy and monetize corporate network access credentials for a share of the profits. The advertisement from this user indicated that the actor was specifically looking for organizations from English-speaking countries, such as the United States, Canada, the United Kingdom, Australia and New Zealand, according to Trend Micro.
A week later, researchers at Trend Micro spotted experts talking about a new ransomware that appends a .basta extension to the encrypted files and changes the desktop wallpaper of the infected system, which allowed them to link the two events.
After buying legitimate network access credentials and infiltrating the victim's systems, Black Basta ransomware still cannot be loaded if it does not have administrator rights to run. It otherwise displays a command prompt message, "Please run as admin," Trend Micro says.
Once the ransomware is successfully run as an administrator, it removes shadow copies, disables Windows recovery and repair, and boots the PC in safe mode, Trend Micro says. It also follows these steps during its infection routine:
- It drops two files, which are used to change the desktop wallpaper and icons for encrypted files.
- Before booting the infected device into safe mode, it changes the desktop wallpaper by dropping the .jpg file into the
%temp%folder and creates a registry entry. - Then, it adds registry keys to change the icon of the encrypted files with the .basta extension.
- Finally, the ransomware encrypts files while the device is in safe mode, appending all encrypted files with the .basta extension. "The ransom note is found in all the folders the ransomware has affected," Trend Micro says.
There are many similarities between Black Basta and Conti, but no conclusive proof of a connection. Trend Micro also notes certain similarities between Black Basta and BlackMatter ransomware, especially its payment sites. "Like BlackMatter, Black Basta implements user verification on its Tor site. However, the leak site does not implement a session key," Trend Micro says.