Business Email Compromise (BEC) , Cybercrime , Cybercrime as-a-service
Beware: AgentTesla Infostealer Now More Powerful
Low-Cost Malware Used in BEC Scams, Other Attacks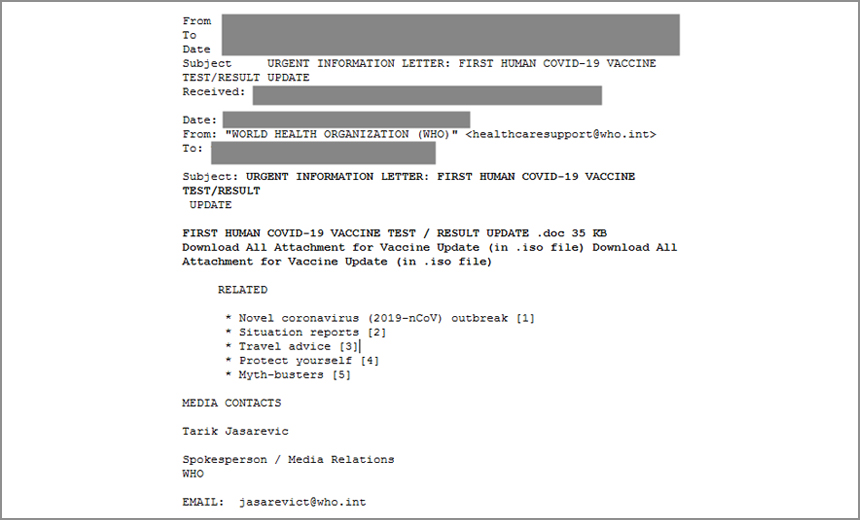
The operators behind the AgentTesla remote access Trojan have upgraded the infostealer with additional capabilities, including the ability to steal credentials from VPNs, web browsers, FTP files and email clients, according to Sentinel Labs.
See Also: The State of Organizations' Security Posture as of Q1 2018
AgentTesla, which was first spotted in the wild in 2014, has recently been used by business email compromise scammers operating out of Nigeria.
Bitdefender reported in April that the infostealer was used in a series of attacks that targeted the global oil and gas industry (see: Attackers Target Oil and Gas Industry With AgentTesla).
Also in April, researchers at Palo Alto Networks' Unit 42 found an increase in COVID-19-themed phishing emails that attempted to deploy AgentTesla across a wide range of industries (see: Fresh COVID-19 Phishing Scams Try to Spread Malware: Report).
AgentTesla is sold to fraudsters and hackers through underground forums, according to the Sentinel One. Low-level hackers commonly use the malware because of its low licensing fees, which range from $12 for a monthly rental to $35 for a six-month lease, the Sentinal Labs report notes.
New Capabilities
Over the past several months, Sentinel Labs researchers have found updated versions of the AgentTesla malware being spread through COVID-19-themed phishing emails. These emails contain either a malicious attachment or a link that downloads the malware.
Researchers note that hackers are using the latest version of the malware primarily to steal credentials from VPNs; FTP files; email services, such as Microsoft Office; and web browsers, including Google Chrome and Mozilla Firefox, the report notes. The malware is also capable of stealing credentials from a registry as well as configuration or support files from the victims’ devices.
"Over time, additional features have been added to AgentTesla," Sentinel Labs researcher Jim Walter notes in the report. "These improvements include more robust spreading and injection methods as well as discovery and theft of wireless network details and credentials."
Attack Tactics
Some of the COVID-19-themed phishing emails used to spread the malware are fraudulently portrayed as coming from the World Health Organization, according to the report (see: 'Hack for Hire' Groups Spoof WHO Emails to Steal Data).
When victims open these emails and click on the malicious link or attachment, the malware exploits a memory corruption and a remote code vulnerability in Microsoft Office, the report states.
The malware is then deployed in various stages of the attack to exfiltrate data, the report notes. Eventually, the infostealer transfers the data to the command-and-control server controlled by the attackers.





















