Anti-Money Laundering (AML) , Endpoint Security , Fraud Management & Cybercrime
Bangladesh Bank Attackers Hacked SWIFT Software
Attackers Used Malware to Steal $81 Million, BAE Systems Says
The attackers who stole $81 million from Bangladesh Bank in February used malware that allowed them to hack into the bank's SWIFT software to transfer money, as well as hide their tracks, according to technology consultancy BAE Systems Applied Intelligence.
See Also: Detect Application & Account Fraud Without Increasing Customer Friction
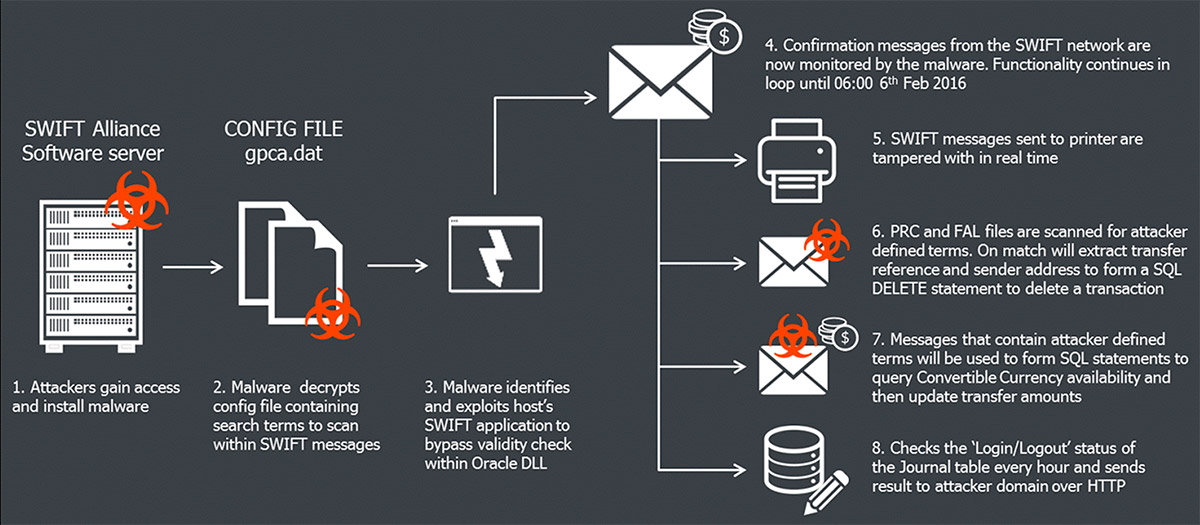
The consultancy notes that it's found "custom malware" developed by an individual based in Bangladesh, which "contains sophisticated functionality for interacting with local SWIFT Alliance Access software running in the victim infrastructure."
SWIFT is a Belgium-based cooperative of 3,000 organizations that maintains a messaging platform that banks use to move money internationally. "SWIFT is aware of a malware that aims to reduce financial institutions' abilities to evidence fraudulent transactions on their local systems," a SWIFT spokesman tells Information Security Media Group. "Contrary to reports that suggest otherwise, this malware has no impact on SWIFT's network or core messaging services."
Any attack that involves SWIFT software, however, is a concern because attackers could literally transfer money from a victim's account into their own. In the case of Bangladesh Bank, for example, the attacker reportedly made 30 SWIFT requests on Feb. 5, using the bank's SWIFT code, in an attempt to transfer $1 billion out of the bank's account at the U.S. Federal Reserve in New York. Ultimately, however, authorities have said that only five of the transfers were successful, totaling about $81 million, and they believe $6.9 million of that money might still be recoverable.
Custom Malware
The malware that targeted Bangladesh Bank, the nation's central bank, was "custom made for this job, and shows a significant level of knowledge of SWIFT Alliance Access software as well as good malware coding skills," says BAE Systems Applied Intelligence security researcher Sergei Shevchenko in a blog post.
For example, the malware was designed not just to alter SWIFT transactions, but also to hide their alterations, since all transfers get sent by SWIFT's software to a printer. "If the fraudulent transaction confirmations are printed out, the banking officials can spot an anomaly and then respond appropriately to stop such transactions from happening," he says. "Hence, the malware also intercepts the confirmation SWIFT messages and then sends for printing the 'doctored' - manipulated - copies of such messages in order to cover up the fraudulent transactions."
News of the Bangladesh Bank malware attack was first reported by Reuters.
Update, Alert Coming From SWIFT
SWIFT says it plans to release software and guidance on April 25 to customers, to help them spot and block related attacks, including altered database records. But it's also stressing to customers the importance of keeping their IT environments patched and up to date, so attackers can't exploit the "weaknesses in their local security" required to install malware (see Solve Old Security Problems First).
"We have developed a facility to assist customers in enhancing their security and to spot inconsistencies in their local database records. However, the key defense against such attack scenarios remains for users to implement appropriate security measures in their local environments to safeguard their systems," the spokesman says.
Malware Alters Oracle Database
Shevchenko at BAE Systems Applied Intelligence says that the malware recovered by his organization - from an undisclosed code-sharing site - only appears to be part of the attack code used by whoever attacked Bangladesh Bank. "This malware appears to be just part of a wider attack toolkit, and would have been used to cover the attackers' tracks as they sent forged payment instructions to make the transfers," he says. "This would have hampered the detection and response to the attack, giving more time for the subsequent money laundering to take place."
Shevchenko warns that the malware and related attack tools used in this attack remain a threat for all SWIFT customers. "The tools are highly configurable and given the correct access could feasibly be used for similar attacks in the future," he says.
He also cautions that "many pieces of the puzzle are still missing" in this attack, including "how the attackers sent the fraudulent transfers, how the malware was implanted, and crucially, who was behind this."
Following the Money
Meanwhile, the broader Bangladesh Bank hack investigation continues. Investigators have reportedly traced all of the missing funds to accounts at Rizal Commercial Banking Corp. in the Philippines, noting that the money appears to have been deposited, then sent by the bank to a foreign exchange service before being redeposited, after which it was withdrawn and then laundered via the country's casinos.
Investigators have focused in part on Maia Deguito, the manager of the RCBC branch into which the money was deposited. Officials say $30 million of the money that the bank received from the foreign exchange service was in the form of banknotes that would have collectively weighed 1,500 kg (3,300 pounds), Reuters reports.
But Deguito has defended herself, telling the country's ABS-CBN television station last month: "I did not do anything wrong. If this is a nightmare, I want to wake up now," Reuters reports.
One colleague of Deguito's, testifying last month before a Senate hearing in Manila, reported seeing her driving off in her car with 20 million pesos ($431,000) in cash, which came from one of the accounts into which the stolen bank funds were transferred, Reuters reports.
Deguito has reportedly declined to publicly testify, with her attorney citing fatigue.
As part of their investigation, prosecutors in the Philippines have launched a criminal investigation against casino operators Kim Wong and Weikang Xu, whose casinos were allegedly used to launder the stolen money.
"Two foreigners were responsible for bringing in the $81 million," Wong told a Senate hearing in Manila last month, who have been named as being Beijing-based Sua Hua Gao, as well as a Macau-based associate identified only as "Ding," Arab Times newspaper reports.






















