Endpoint Security , Governance & Risk Management , Internet of Things Security
Backdoor Discovered in Xplora Children's Smartwatch
Chinese Manufacturer Issues a Patch to Remove the Code
A smartwatch intended to help parents keep close tabs on their children shipped with a backdoor that could be activated remotely by an encrypted SMS, causing the device to secretly take screenshots.
See Also: How to Improve OT/IoT Network Visibility
The smartwatch is manufactured by Chinese company Qihoo 360, which was one of two dozen companies that, as of May, can no longer receive exports of U.S. technology unless an exporter seeks permission from the U.S. Department of Commerce, due to national security reasons.

The Norwegian security firm Mnemonic dissected the smartwatch, which doesn’t carry Qihoo 360 markings and is branded as the Xplora 4.
“The device is a wearable smartphone, and the backdoor enables remote and covert surveillance through wiretapping, taking pictures and location tracking,” write Harrison Sand and Erlend Leiknes, security researchers with Mnemonic, who describe their technical findings in a blog post.
The Xplora 4 is sold in Nordic countries, the U.K., Spain, Germany, France and Poland. As of this month, the Xplora 5, which starts at $190, began selling in the U.S. Xplora claims to have more than 400,000 users. The watches are marketed in Europe and the U.S. by Xplora Technologies AS.
In a statement, Xplora says it deployed a patch on Thursday that removes the backdoor.
"We conducted an extensive audit since we were notified and have found no evidence of the security flaw being used outside of testing,” the company says.
The discovery of the flaw adds to a string of worrying security discoveries about kids’ smartwatches. They’re sold under the pretense that parents can enjoy peace of mind by tracking their child’s whereabouts and having the ability to call their child (see: Australian Kids' Smartwatch Maker Hit By Same Bug Again).
Sneaky Screenshots
The Mnemonic researchers say the wearable smartphone uses a SIM card with a number, has a two-way microphone and can transmit GPS location data. Parents can also set alerts if their child deviates from a geofenced zone.
The device runs on Android Nougat and has a Qualcomm Snapdragon Wear 2100 processor. The researchers used a Qualcomm feature called EDL to download the device’s data from flash memory.
The Mnemonic researchers then browsed the 90 applications on the device, most of which were either Android or Qualcomm code. The remainder of the applications were developed by Qihoo 360, they write.
They found a suspicious application called “Persistent Connection Service.” It goes through all of the other applications on the device and creates a set of intents that can be called upon. The researchers then found intents that has been coded into the Qihoo contact application with very suspicious file names: WIRETAP_INCOMING and WIRETAP_BY_CALL_BACK.
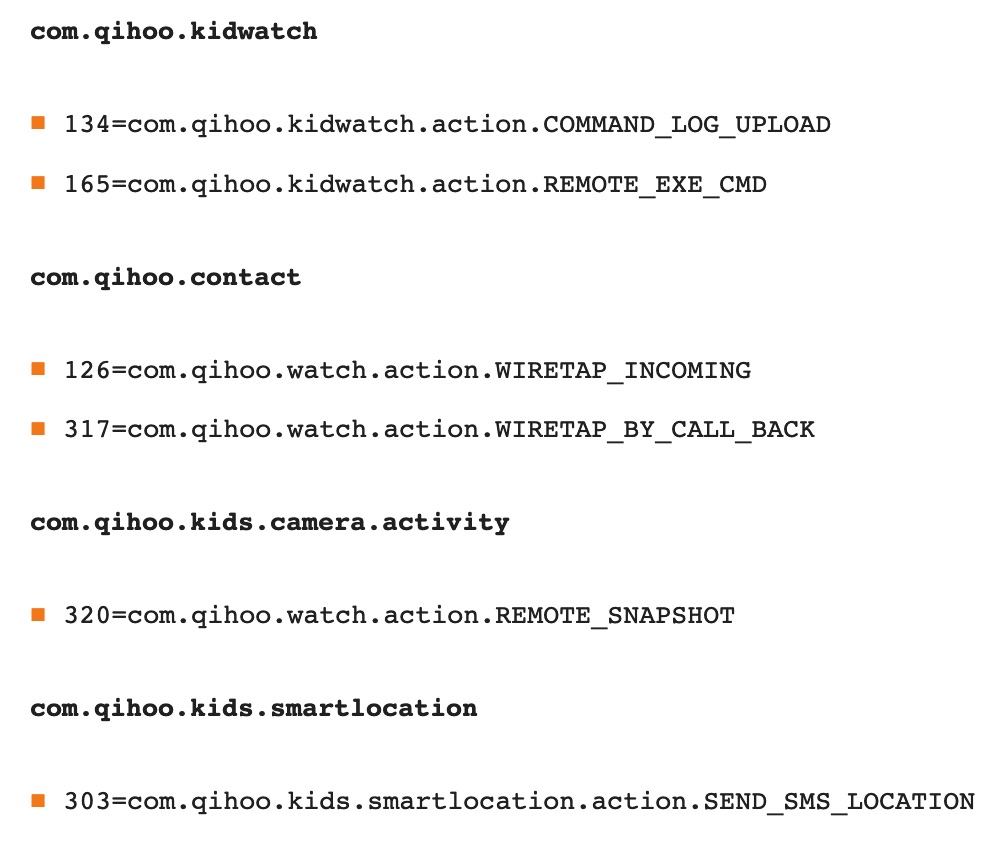
Eventually, the Mneumonic researchers discovered that "an encrypted SMS can be sent to the watch to trigger the surveillance functions."
The researchers discovered the RC4 encryption key for the SMS message, which allowed them to activate the remote snapshot feature. Upon receiving the encrypted SMS, the watch takes a photo without alerting the user and sends it to Xplora’s servers.
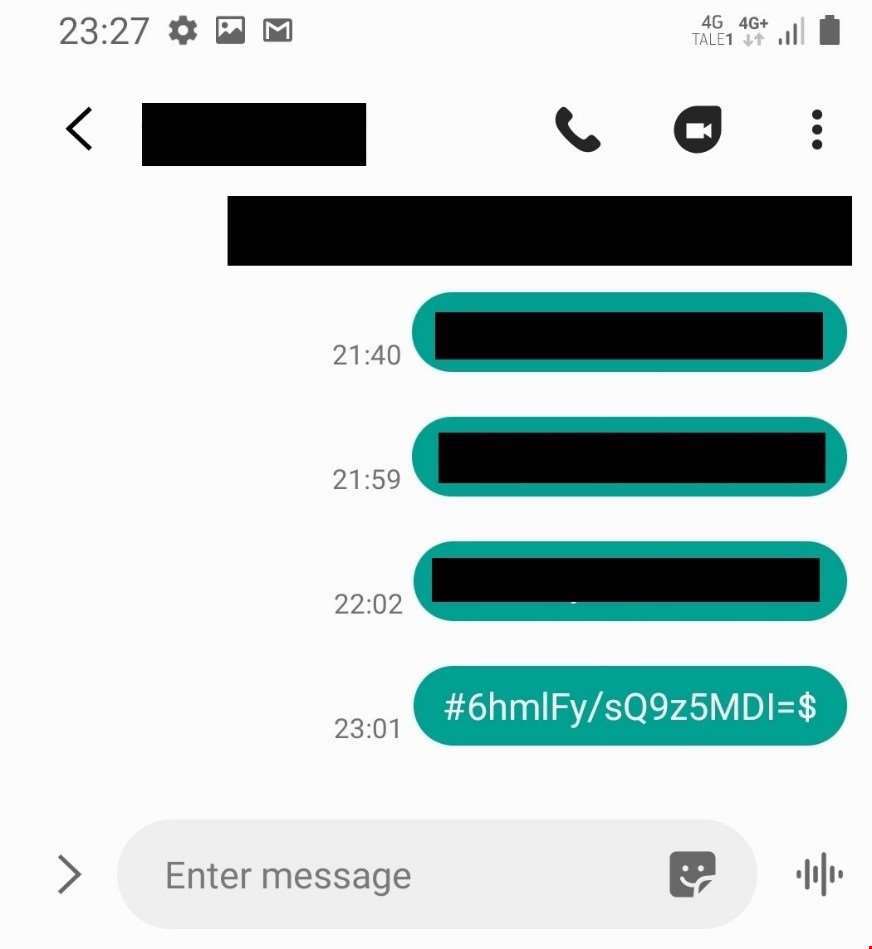
For an attacker to do this, however, they would need the victim’s phone number and also hardware access to pull the RC4 key.
Sand and Leiknes write that some diagnostic data was sent to Qihoo’s servers in China, although it appears a smartwatch’s phone number wasn’t collected. But there was a certain amount of either obfuscated or encrypted code that researchers couldn’t figure out.
Even though one attack scenario calls for getting the RC4 key via possession of a device, “because the key is set during production, we can safely assume that Qihoo 360 has this key. This includes personnel at the factory where the watch was made,” the Mnemonic researchers say.
Xplora: Prototype Code Left in
The manufacturer has an explanation for how the code ended up on the smartwatch. It says parents wanted to be able to reach their children during an emergency, such as in a kidnapping scenario. So, the ability to take a secret snapshot was wrapped into the smartwatch as part of a prototype, along with other features.
“In the end, Xplora decided not to include any of these features in the commercial release due to privacy concerns and removed the capability to access these features and removed the code and functionality for all commercial models due to privacy concerns,” Xplora says. “The researcher found some of the code was not completely eliminated from the firmware.”
Even if someone else replicated what Mnemonic did, Xplora says a screenshot taken through the encrypted SMS feature “is only uploaded to Xplora’s server in Germany and is not accessible to third parties.”



















