Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
APT Group Targets Fintech Companies
Report: Little-Known Evilnum Group Relies on Spear-Phishing Emails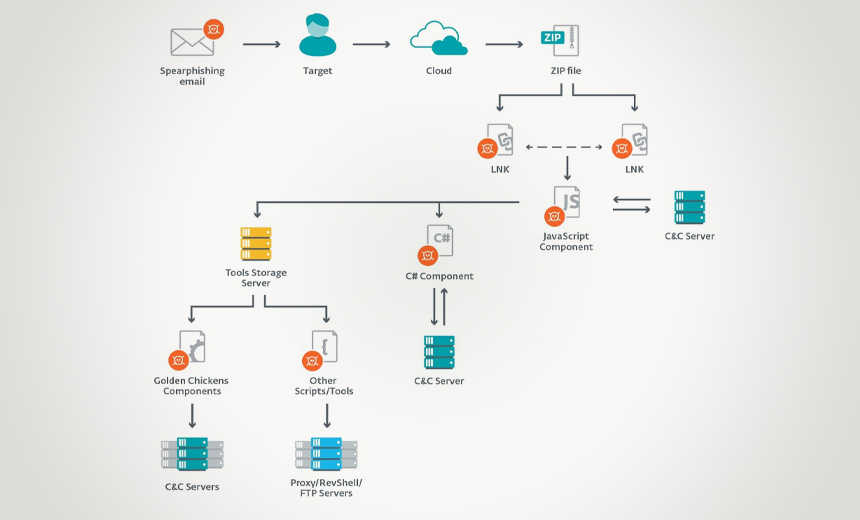
A little-known advanced persistent threat group dubbed Evilnum has been targeting fintech firms in the U.K. and Europe over the past two years, using spear-phishing emails and social engineering to start their attacks, according to the security firm ESET.
See Also: The State of Organizations' Security Posture as of Q1 2018
In a report released Thursday, ESET researchers say the group recently expanded its targets beyond British and other European firms to companies in Canada and Australia. The report did not name any of the targeted companies.
"According to ESET's telemetry, the targets are financial technology companies - for example, companies that offer platforms and tools for online trading," the researchers note. "Typically, the targeted companies have offices in several locations, which probably explains the geographical diversity of the attacks."
The APT group is believed to use a malware strain that is also called Evilnum, but is sometimes referred to as CardinalRAT and CarpDownloader, according to ESET.
This JavaScript malware was first spotted in 2018 by Palo Alto Networks' Unit 42 and had previously targeted Israeli fintech companies. The Evilnum malware steals a wide variety of information, including customer records, credit card numbers and a device's Microsoft license number, the report notes.
The spear-phishing emails the APT group uses attempt to infect devices with the Evilnum malware as well as other types of malicious code purchased or rented from other hacking groups.
The ESET report does not draw a conclusion as to where the Evilnum group is based. But it's likely the threat actors have had some success targeting fintech firms since their activities began in 2018, says Matias Porolli, an ESET threat researcher.
"Judging by the fact that the attacks are targeted and the potential victims are approached with specific - not mass-sent - emails, we believe the attackers were successful in their efforts," Porolli tells Information Security Media Group.
Infection Tactics
Evilnum's first step is sending out spear-phishing emails to technical support representatives and account managers within the target organization with financial document attachments as a lure, the researchers note.
When the victim opens the email, a Zip archive extracts and executes a malicious LNK file - a shortcut used in Windows - that runs a JavaScript component and also displays a decoy document, the report notes.
"The documents used as decoys are mostly photos of credit cards, identity documents, or bills with proof of address, as many financial institutions require these documents from their customers when they join, according to regulations," the report notes.

The ESET researchers also point out that these documents appear to be genuine and may have been collected by the threat actors from various sources to add legitimacy to their attacks.
Once the targeted victim clicks on the LNK file to view one of the documents, the malware begins to load in the background and infect their device, according to the report.
Once the attackers successfully infect devices and a network, the malware steals sensitive corporate data, such as customer lists, credit card information and other personally identifiable data, along with the firm's investments and trading operations data, the ESET researchers report.
In the next phase of the attack, the JavaScript components deploy other malware the Evilnum operators purchased from other hackers, including code written in C# from the malware-as-a-service provider Golden Chickens, the report notes. The attackers also use Python-based tools in their toolkits, the researchers add.
While the JavaScript component acts as a backdoor and handles communications with the command-and-control server, the C# code takes on other tasks, including grabbing a screenshot whenever the mouse is moved over a certain length of time, sending system information back to the operators as well as stealing cookies and credentials. Eventually, this process will kill the malware when the campaign is complete, according to the report.
The attackers then use a number of additional Golden Chicken tools to perform anti-debugging techniques and identify anomalies in order to identify a sandbox. If one is spotted, this technique will prevent the code from executing to help prevent detection, the researchers add. These tools also help the attackers collect data from victims’ email applications and gain additional persistence, according to the report.
In the final stage of the attack, the group deploys a Python-based infrastructure to take additional screen shots, perform key-logging and collect data. The malware then snatches the device's Microsoft Office and Windows licenses and sends them to the command-and-control server.
Rise in APT Attacks
Since the start of the COVID-19 pandemic, APT groups have turned their attention to large enterprises, security experts note.
For example, an April report from security firm Malwarebytes found that APT groups with links to China, Russia and North Korea were using new tactics to target an increasing number of victims.
In May, U.S. and U.K. authorities warned that APT groups are using "password spraying campaigns" to target medical institutions, pharmaceutical companies, universities and others conducting COVID-19 research (see: Alert: APT Groups Targeting COVID-19 Researchers).






















