Application Security , Cybercrime , Fraud Management & Cybercrime
APT Group Kimsuky Has New Attack Technique, Researchers Say
South Korean Government Reportedly Targeted Using AppleSeed Backdoor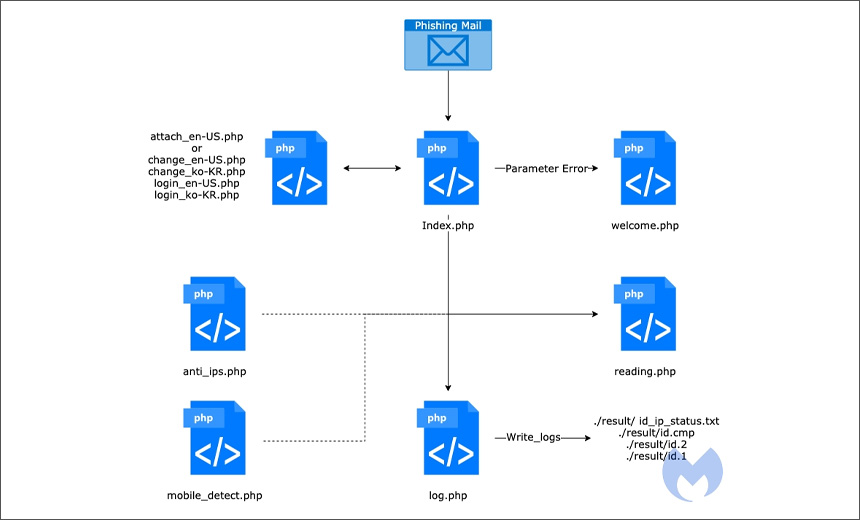
Researchers at Malwarebytes have uncovered the latest tactics, techniques and procedures used by the North Korean threat group Kimsuky, also known as Thallium, Black Banshee and Velvet Chollima, as it continues to launch espionage attacks. This time it is using an AppleSeed backdoor.
See Also: Cybersecurity for the SMB: Steps to Improve Defenses on a Smaller Scale
The Kimsuky group, which has been active since 2012, primarily focuses on government entities in South Korea, but also conducts espionage campaigns against targets in the U.S. and Japan.
The Malwarebytes Threat Intelligence team has been monitoring Kimsuky activities and was able to spot its phishing websites, malicious documents and scripts used to target high-profile people within the government of South Korea.
The Kimsuky group can set up phishing infrastructure to effectively mimic well-known websites and trick victims to enter their credentials, researchers say.
"This is one of the main methods used by this actor to collect email addresses that later will be used to send spear-phishing emails," researchers note.
AppleSeed Backdoor
The researchers found that Kimsuky reuses some of its phishing infrastructure for its command-and-control communications. In one of the attacks against South Korea’s government, it reused the infrastructure that had been used to host its phishing websites for AppleSeed backdoor C2 communications.
The initial infection was achieved by the actor distributing its dropper embedded in an archive file (외교부 가판 2021-05-07.zip) as an attachment through spear-phishing emails. The target email addresses were collected using the actor email phishing campaigns. The actor conducted this spear-phishing attack on May 7, 2021.
"The archive file contains a JavaScript file (외교부 가판 2021-05-07.pdf.jse) which pretends to be a PDF file containing two Base64 encoded blobs. The first one is the content of the decoy PDF file in Base64 format and the other one contains the AppleSeed payload, also in Base64 format (encoded twice). At first it uses the MSXML Base64 decoding functionality to decode the first layer and then it uses certutil.exe to decode the second layer and get the final AppleSeed payload. The decoy PDF file has been decoded using the MSXML Base64 decoding function," Hossein Jazi, a security researcher at Malwarebytes, says.
The payload ultimately leads to the deployment of an encoded DLL payload called AppleSeed. The DLL file is packed using the UPX packer. The unpacked sample is highly obfuscated, and important API calls and strings have been encrypted using a custom encryption algorithm.
Apart from using the AppleSeed backdoor to target Windows users, the actor has also used an Android backdoor to target Android users. Researchers note that this Android backdoor can be considered as the mobile variant of the AppleSeed backdoor.
"It uses the same command patterns as the Windows one. Also, both Android and Windows backdoors have used the same infrastructure," Jazi notes.
Upon successful installation of the payload, AppleSeed performs its main functions in separate threads, which include collecting data and zipping and encrypting it to send it to the command-and-control server using HTTP POST requests in a separate thread.
”After sending the data to the server, the data is deleted from the victim’s machine," researchers note.
AppleSeed is capable of recording keystrokes, capturing screenshots, collecting documents and finding the removable media devices connected to the machine and collects its data before sending it to the C2 server.
High-Profile Targets
Malwarebytes reports that Kimsuky used “외교부 가판 2021-05-07”, one of the lures in the Korean language that translates to “Ministry of Foreign Affairs Edition 2021-05-07” - which indicates that it has been designed to target the Ministry of Foreign Affairs of South Korea.
In addition to the Ministry of Foreign Affairs, Kimsuky also targeted the Republic of Korea 1st Secretary, Ministry of Foreign Affairs, Republic of Korea 2nd Secretary, Trade Minister, Deputy Consul General at Korean Consulate General in Hong Kong, International Atomic Energy Agency Nuclear Security Officer, Ambassador of the Embassy of Sri Lanka, Ministry of Foreign Affairs and Trade Counsellor.
Researchers also observed that Kimsuky collected information about universities and companies in South Korea, including the Seoul National University and Daishin financial security company as well as the Korea Internet and Security Agency. "This does not mean the threat actors actively targeted them yet nor that they were compromised," researchers note.
Analysis of Updated Attack
Malwarebytes states that the operators behind Kimsuky have added Mobile detect and Anti IPs modules to be able to detect mobile devices and adjust the screen view based on that. It can show phishing pages in English or Korean based on the parameter value received from the phishing email.
Last year, security firm Cybereason uncovered malicious tools tied to the North Korean-linked hacking group.
The Kimsuky-linked tools included a modular spyware suite called "KGH_SPY," a malware downloader dubbed "CSPY Downloader," and additional infrastructure that overlaps with a previous campaign that targeted a U.S. think tank in 2018 (see: Additional Hacking Tools Tied to North Korea-Linked Group).
Researchers observed that Kimsuky operators developed different phishing techniques to mimic web services and steal credentials from Gmail, Hotmail, Microsoft Outlook, Nate, Daum, Naver, Telegram and KISA. They identified several URLs used by Kimsuky to host their phishing infrastructure.
Malwarebytes reports that the operators used Twitter accounts to find and monitor their targets to prepare customized spear-phishing emails.
"The group is also using Gmail accounts for phishing attacks or registering domains. One of the Gmail accounts used by this actor is 'tjkim1991@gmail[.]com' which was used to register these domains ns1.microsoft-office[.]us and ns2.microsoft-office[.]us," the researchers report.
The domains were registered on April 3 and have been reserved to be used for future campaigns, the researchers say, adding: "Pivoting from these domains, we were able to uncover the infrastructure used by this actor. Some of it has overlap with previously reported campaigns operated by Kimsuky."





















