Anti-Phishing, DMARC , Email Threat Protection
Phishing Scam Targets Apple Users
Campaign lllustrates Trend of Fraudsters Using Global Brands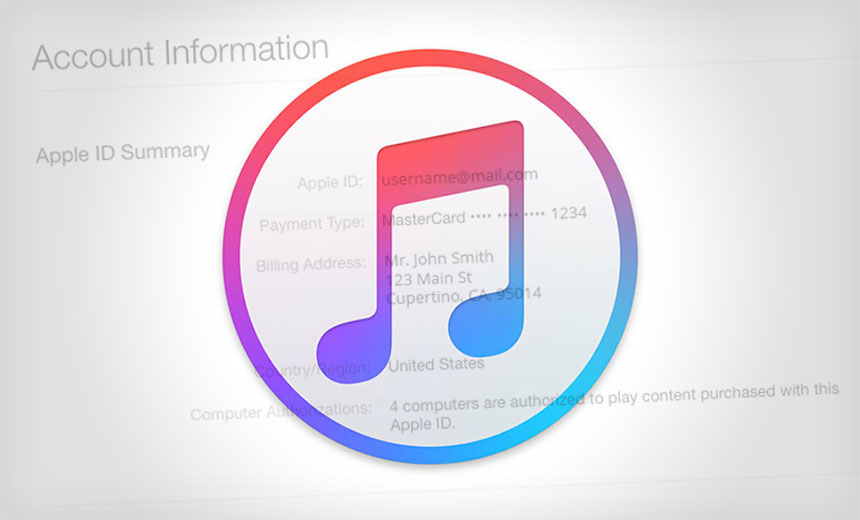
(This story has been updated.)
"Good things come to those who bait."
That's one phishing attack truism, courtesy of the Verizon 2015 Data Breach Investigations Report, released earlier this year, which warns that fake emails continue to be a favorite tool of cybercriminals and nation-state attackers. Despite widespread knowledge of the problem, the median time between a phishing campaign starting and at least one victim clicking an attachment is just 82 seconds.
Blocking such attacks at their source has proven impossible - at least to date - given the massive malicious infrastructure apparatus involved. The Anti-Phishing Working Group reports that on a monthly basis, it's tracking more than 9,000 phishing domains and almost 50,000 phishing URLS.
Meanwhile, fraudsters and espionage operators continue to refine their attacks. And it's no surprise that they're increasingly employing must-have technology or global brands to entice consumers into infecting themselves with malware, or divulging personal or account details that attackers can use to take control of financial accounts.
The latest in a long line of such scams is a campaign targeting Apple users, according to researchers at online security firm Comodo. The phishing messages, which appear to come from Apple, instruct the recipient to update their Apple account by verifying credit card information and passwords, Comodo says in a Nov. 9 blog post.
The phishing attack is hardly novel: To update their accounts, recipients of the email are asked to click a link that directs them to a fake Apple webpage. From there, the information provided by the users is captured by fraudsters, Comodo says.
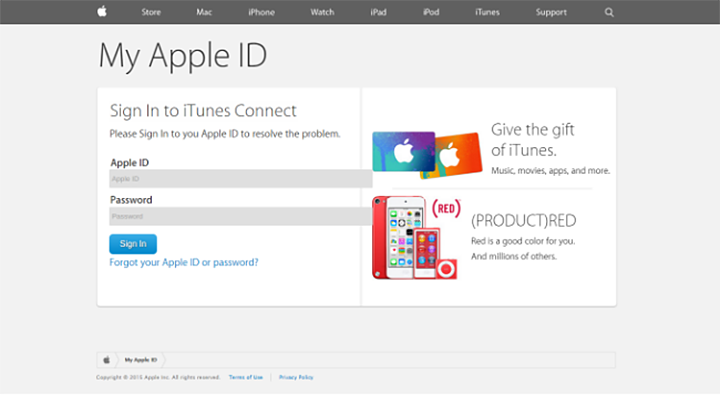
Analysis Reveals Scam
The Comodo Antispam Labs team identified the Apple phishing email through analysis of Internet protocol addresses, domains and URLs, says Fatih Orhan, Comodo's director of technology and head of the firm's Antispam Labs.
"This wasn't really an attack per say, but more of a phishing expedition in the truest sense of the word," Orhan says. "That's what email phishing does - it waits for the person to bite on the fraudulent email. Comodo and our Antispam Labs team noticed this uptick in Apple-ID-related malware only a few days ago, tracked it, and then saw an emerging pattern that we felt was important to flag."
Orhan says Comodo does not know if any Apple users have fallen for the attack, or if fraud has resulted. But he says given the size of Apple's customer base, which includes some 800 million iTunes users, the campaign could be far-reaching.
"Cyberthieves, who specialize in phishing, play the odds that a consumer or business will submit the information they are phishing for," Orhan says. "The larger the brand, the more people who are apt to be interacting with that brand in some way, shape or form."
Apple did not respond to Information Security Media Group's request for comment about the phishing campaign.
Need for Vigilance
According to Verizon's breach report, 23 percent of all phishing message recipients open the message and 11 percent click on an attachment.
Of course, not all such campaigns are focused on targeting individuals solely for the purpose of fraud. While early phishing attacks typically focused on account takeovers and committing fraud, by 2013, 95 percent of all state-sponsored attacks spotted in the wild employed a phishing component that was typically employed to facilitate a malware infection, Verizon says. As a result, falling for a phishing scam may lead to not just account fraud, but the theft of sensitive personal information, intellectual property, ransomware, extortion, state secrets and more.
"Lessons not learned from the silly pranks of yesteryear and the all-but-mandatory requirement to have email services open for all users has made phishing a favorite tactic of state-sponsored threat actors and criminal organizations, all with the intent to gain an initial foothold into a network," Verizon's report says.
In this hostile climate, companies must somehow still attempt to safeguard their brands, experts say (see Spear Phishing: A Bigger Concern in 2015).
But there's relatively little that governments, businesses whose brands get targeted or banking institutions can do to directly prevent consumers from falling for these types of attacks, contends Dave Jevans, chairman of the Anti-Phishing Working Group, a global organization that monitors phishing trends, and vice president mobile security at Proofpoint.
The latest scam targeting Apple users is similar to many earlier phishing attacks that have targeted users of PayPal, Gmail, eBay, Hotmail and many others, he says. "They are large and ongoing and will never stop. This is why companies deploy world-class email threat detection and prevention."
Of course, the same cannot be said for every business or consumer.
Furthermore, technology alone cannot solve the problem. The MITRE Corp., which manages U.S. federally funded labs, reports that 10 percent of all phishing attacks are spotted by end users, meaning those messages had successfully penetrated its email gateway defenses.
That's why Apple, amongst others, tries to educate its customers about emerging threats, for example via a webpage devoted to phishing and other suspicious emails, Jevans says. But Apple, or any other brand, can only do so much to prevent consumers from willingly providing account information to fraudsters, he adds. "Phishers continue to target the low-hanging fruit on the consumer side."
Fast Fraud
So phishing attacks likely will remain an easy way for attackers to make a quick buck. Al Pascual, director of fraud and strategy at Javelin Strategy & Research, says once consumers cough up passwords and credit card information, it's difficult to prevent criminals from using the compromised credentials to commit fraud, and not just online. For example, while Apple has enhanced its authentication and enrollment methods for Apple Pay, Pascual says compromised credentials could undermine many of those verification mechanisms Apple put into place.
Banks and Apple shored up Apple Pay enrollments to ensure that the accounts are "essentially fraud-free," Pascual says. But, he adds, "this new scheme could undermine that significantly, illustrating that every point in the payment system will be tested by new attacks, even those in mobile."
Combating Phishing Campaigns
As phishing attacks - and targets - evolve, so too must defenses. Lance Spitzner, a training director for the SANS Institute, recommends combating phishing campaigns via "effective awareness and training."
Many experts also recommend employing some type of crowd-sourced technology that enables end users to flag suspicious messages, so they can be blocked for other recipients before they might inadvertently click on the malicious message or any attachments.
Executive Editor Mathew J. Schwartz also contributed to this story.