Fraud Management & Cybercrime , Fraud Risk Management , Social Engineering
Android Trojan Targets European Bank Customers
Cleafy: TeaBot Steals Credentials and SMS Texts From Victims to Use for Financial Fraud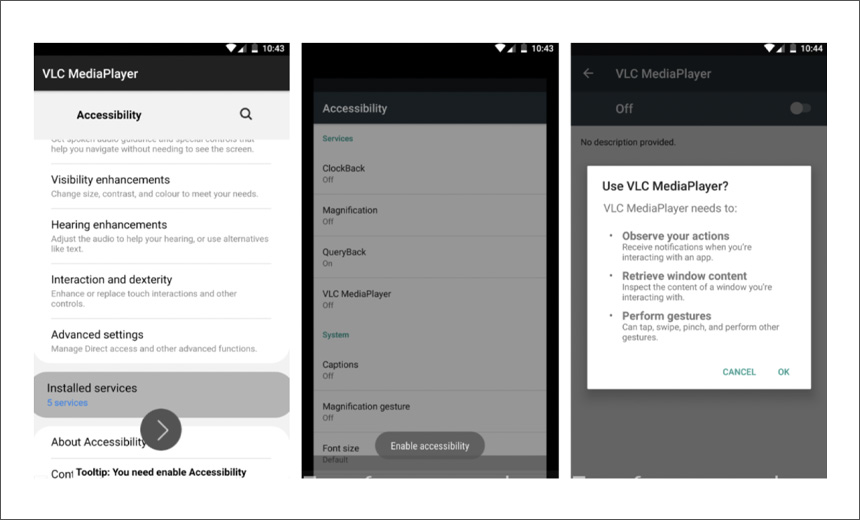
A newly uncovered Android Trojan called TeaBot is targeting bank customers in Europe to steal sensitive credentials and SMS texts for financial fraud, a report by security firm Cleafy notes.
"At the beginning of January 2021, a new Android banking Trojan was discovered and analyzed by our Threat Intelligence and Incident Response team," Cleafy says. "We decided to dub this new family as TeaBot since it seems to not be related to any known banking Trojan family."
Cleafy tells Information Security Media Group that TeaBot is distributed via social engineering schemes. “We detected that the main vector used by bad actors are smishing campaigns [phishing via SMS], where the victims are persuaded to download and install the distributed malicious application.”
Initially, the malware was hidden in malicious apps portrayed as being TeaTV, a movie-watching app. In the last month, the attackers shifted to Trojanized versions of VLC MediaPlayer, Mobdro, DHL, UPS and bpost apps, Cleafy reports. Once the malicious app is successfully installed, the researchers say that the malware steals SMS texts related to banking details, accesses contacts and can modify audio settings and delete installed apps.
TeaBot initially targeted customers of Spanish and Italian banks, but since March, it's been targeting bank customers in Italy, Belgium and the Netherlands, Cleafy reports. It supports six languages: Spanish, English, Italian, German, French and Dutch.
Data Exfiltration
Cleafy says the main purpose of TeaBot is to exfiltrate data. Once the malware has been inadvertently installed by a victim by downloading what looks like a legitimate app, attackers obtain livestreaming of the victim's device screen and can interact with it by abusing accessibility services designed to assist users with disabilities.
The malicious apps are downloaded as an Android service, which helps the malware to disguise itself and gain persistence. The malware then acts as a dropper, dynamically loading second-stage malware. That malware then observes a user's interactions and retrieves content, then establishes contact with the attackers' command-and-control server.
"TeaBot, during its first communications with the C2, sends the list of installed apps to verify if the infected devices had one or more targeted apps already installed," the report notes. "When TeaBot finds one of them, it downloads the specific payload to perform overlay attacks and starts tracking all the activity performed by the user on the targeted app. This information is sent back to the assigned C2 every 10 seconds."
Although the attackers have deployed the malware in several campaigns, the report notes TeaBot is still in the developmental stage.
When asked if there's evidence of fraud resulting from the use of TeaBot, Cleafy said it was unable to disclose any information on this issue.
Similar Campaigns
In April, security firm Doctor Web reported that more than 500,000 Android devices across the world had been targeted through malicious apps in AppGallery, the official app store of Huawei (see: Joker Malware Targets More Android Devices).
In September 2020, the Joker malware was found to be targeting Android users via malicious apps in Google Play as well as third-party app stores (see: Fresh Joker Malware Variant Targeting Android Users).
Other malware has also been targeting Android users. For example, over the past five years, a sophisticated spyware campaign dubbed PhantomLance has been targeting Android users through Trojan-laced apps in the Google Play Store that are disguised as various plug-ins, browser cleaners and application updaters, according to a report Kaspersky published in April (see: Spyware Campaign Leverages Apps in Google Play Store).
In July 2020, Malwarebytes reported fraudsters were inserting a Trojan called Cerberus within a money converter app to target Android devices (see: Cerberus Banking Trojan Targeted Spanish Android Users).






















