Cybercrime as-a-service , Fraud Management & Cybercrime , Ransomware
7 Trends: How Ransomware Operations Continue to Evolve
New Players and Rebranding Remain Constant, as Does Challenge of Operating Anonymously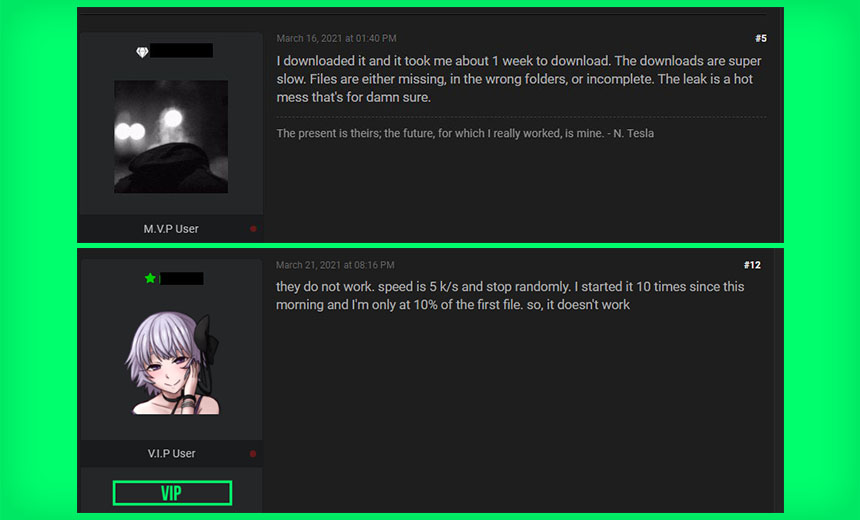
Ransomware continues to be many criminals' weapon of choice for reliably shaking down victims small, medium and large, in pursuit of a safe, easy and reliable payday.
But the ransomware landscape itself continues to evolve in numerous ways. For example, the arrival of new players remains constant, while big names occasionally bow out. Some gangs run complex ransomware-as-a-service operations, tapping specialists in network penetration, negotiations, malware development and more. Many others, however, lack the budget and staffing necessary to reliably take down big targets, so they operate on the periphery. And while many operations run their own data-leak sites, even these come with operational challenges.
As ransomware attacks continue, here are seven ways the ecosystem continues to evolve:
1. Groups Rise and Fall
Security firms continue to track a steady amount of churn in the ransomware-attacker space, including an influx of fresh faces or at least names.
Going dark in Q3 were Avaddon, Noname, relative newcomer Prometheus and REvil, aka Sodinokibi. But REvil returned in September, before disappearing again, last month, potentially due to being disrupted by law enforcement authorities.
Also in Q3, new players - or at least names - appeared, including CryptBD, Grief, Hive, Karma, Thanos and Vice Society, Cisco Talos security researchers David Liebenberg and Caitlin Huey write in a blog post.
2. Rebranding Is Common
Some of those supposedly new operations, however, may simply be existing groups that rebranded. In Q3, for example, "the SynAck ransomware group, which hosted a data leak site called 'File Leaks,' rebranded itself as 'El_Cometa,'" Ivan Righi, a cyberthreat intelligence analyst with Digital Shadows, says in an analysis of Q3 trends.
"The DoppelPaymer ransomware was found to likely have rebranded as the 'Grief' ransomware group, and it is believed that the Karma ransomware group is a rebrand of the Nemty ransomware gang," he adds.
3. Attacks Spread Among Many Groups
Regardless of names, a greater number of players in Q3 appeared to be involved in a greater volume of the attacks being seen, the Cisco Talos researchers say. In particular, of the incident response engagements Cisco Talos worked, only Vice Society and REvil were seen across more than one engagement, they say, "highlighting greater democratization of emerging ransomware variants."
Not seen by Cisco Talos during any engagement, despite previously having been prolific: Ryuk. "Many security researchers believe the Conti ransomware family is a successor to Ryuk, potentially explaining the decline in observations of Ryuk activity," Liebenberg and Huey of Cisco Talos say.
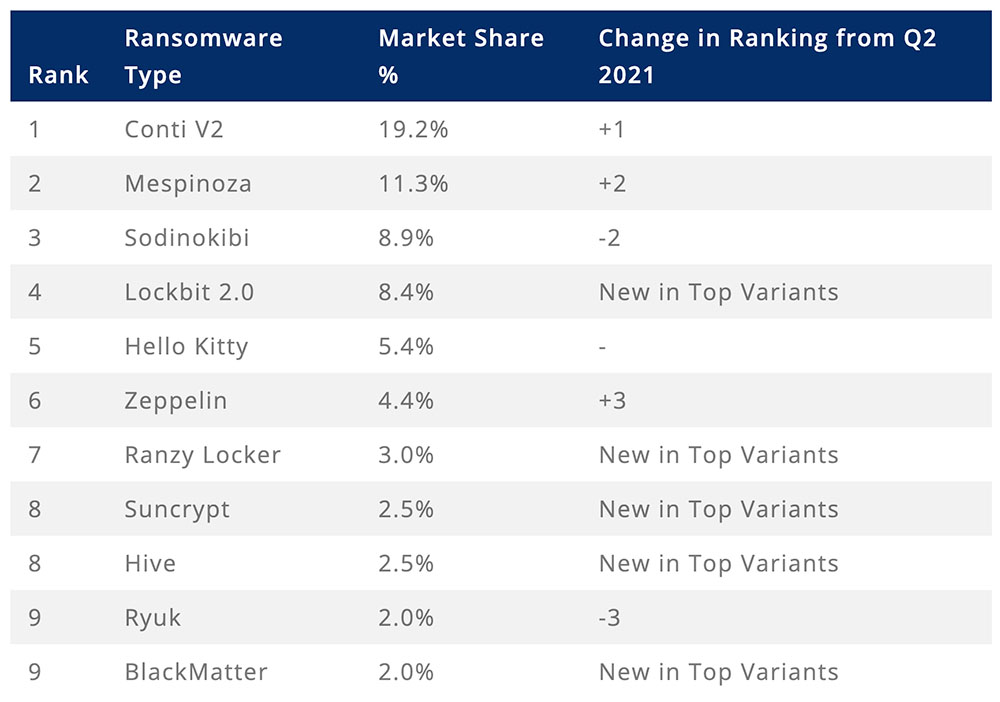
Those findings largely square with what other firms have been recording. Ransomware incident response firm Coveware, for example, recorded a sharp rise in Conti attacks and a decrease in Ryuk attacks, based on thousands of cases with which it assisted during Q3. Because the firm helps victims with incidents that do not always become public, it's likely one of the more accurate assessments of what's actually happening in the wild.
4. Ransomware Operators Are Not All Big Earners
A large number of ransomware groups appear to remain active. Just since Oct. 25, for example, Israeli threat intelligence firm Kela reports that 11 groups have listed victims on their data leak portals: Avos Locker, BlackByte, BlackMatter, Clop, Conti, Grief, LockBit, Marketo, Midas, Pysa and Xing.
Some are bagging big bucks. During Q3, when a business, government agency or any other organization opted to pay a ransom, on average it paid $140,000, according to Coveware, based on thousands of cases it helped investigate. While that average remained steady from Q2, it notes that in the same time frame, the median payment increased by more than 50%, suggesting that attackers have begun to focus more on smaller and midsize victims, after the Biden administration this past summer announced a crackdown on ransomware.
But McAfee researcher Thibault Seret, in a blog post, notes that not every ransomware-as-a-service operation is seeing six-figure ransom payoffs, or more.
"Going by recent headlines you could be forgiven for thinking all ransomware operators are raking in millions of ill-gotten dollars each year from their nefarious activities," he says. "Lurking in the shadows of every large-scale attack by organized gangs of cybercriminals, however, there can be found a multitude of smaller actors who do not have access to the latest ransomware samples, the ability to be affiliates in the post-DarkSide RaaS world or the financial clout to tool up at speed."
5. Malware Leaks Feed Smaller Players
But smaller operations can be innovative in other ways. For example, Seret details how the June leak of the builder for Babuk ransomware was seized on by some as a building block for rolling their own, more advanced crypto-locking malware.
But in another case, he says, attackers previously tied to .NET ransomware called Delta Plus simply tweaked the Babuk ransom note - inserting bitcoin wallet addresses that they, not Babuk, controlled, for victims to pay a ransom - and then used it to target victims. With this new, albeit only slightly tweaked malware, he notes, the attack group began demanding ransoms not worth hundreds of dollars, but rather thousands.
6. Leaking Stolen Data Brings Challenges
While stealing data from a victim and threatening to leak it is a strategy widely practiced by ransomware gangs, it's not foolproof. Challenges are that a victim may of course still opt to not pay - and if an attacker didn't steal sensitive data, perhaps even more so. In addition, hosting the data also turns out to be fraught with challenges, Digital Shadows' Righi says in a blog post.
"Many ransomware groups have experienced difficulties managing data leak sites and hosting data on the dark web for download," he says. "This has resulted in some ransomware groups exposing data using public file-sharing websites, such as Mega[.]nz or PrivatLab[.]com. As these services are hosted on the clear web, they can often be taken down, and most download links are removed within a day or two."
Another challenge, he notes, is that dark web sites - meaning sites only reachable via the anonymizing Tor browser - are designed to prioritize privacy over performance. Therefore, navigating the dark web can be slow, and attempting to download leaked data can be an exercise in frustration.
Or at least that's what many users of the XSS Russian-language cybercrime forum reported, when they attempted to download data leaked in March by the Clop ransomware operation, which had stolen it from security firm Qualys.
"The download speeds were so slow that some users claimed it took them nearly one week to download the first dataset, while other users reportedly gave up," Righi says.
Hosting data leak sites and payment portals also makes them a target for law enforcement agencies. That's what appears to have happened to REvil, when an administrator rebooted the operation's Tor-based sites, only to find that someone else - perhaps a former administrator, perhaps a law enforcement official, perhaps both - also had a copy of the setup files, allowing them to hijack REvil's Tor sites (see: Ransomware Soap Opera Continues With REvil's Latest Outage).
7. Operators Risk Unmasking
Some ransomware operations appear to be especially big earners, thanks in part to some victims paying cryptocurrency ransoms worth millions of dollars.
Last week, weekly German newspaper Die Zeit reported that German police believe they've identified a suspected leader of REvil, a self-described bitcoin entrepreneur called "Nikolay K." - not his real name - thanks in part to tracing cryptocurrency tied to an attack by GandCrab, which was REvil's former incarnation. Police reportedly identified him after following $17,000 worth of cryptocurrency believed to have been paid to GandCrab in 2019 by one of its victims, the Staatstheater in Stuttgart, and finding it was tied to an email account used by Nikolay K.
If he is a REvil administrator, Die Zeit reports, that would help explain a lavish lifestyle, documented on social media by his wife, that includes yacht holidays, a luxury Vanguard Encrypto watch on his wrist and a high-end BMW in the driveway.
But a ransomware-driven lifestyle and attempts to remain anonymous might also take their toll on practitioners.
On Oct. 22, for example, the administrator of Groove ransomware, who goes by Orange - as well as TetyaSluha and boriselcin, for Russia's first elected president, Boris Yeltsin - posted a message on Groove's data leak site, claiming the whole effort had been an experiment designed to "troll" Western media. The message was cross-posted by boriselcin on the XSS cybercrime forum.
His posts "claimed that there is no such thing as the Groove gang, and that behind the whole affair was one person, who has worked with many ransomware affiliate programs, including BlackMatter, LockBit and others," Victoria Kivilevich, director of threat research at Kela, tells Information Security Media Group. "The author claims that he was asked to write an article about mass media manipulation, and the Groove site was created just for that."
John Fokker, the principal engineer and head of cyber investigations for Advanced Threat Research at McAfee Enterprise, recommends treating all criminal claims with a heavy dose of skepticism. "Regardless if Groove is a hoax or not, they or he - Orange - can be linked to multiple breaches. So it is definitely not a hoax for the victims," he says (see: Ransomware Evolves: Affiliates Set to Wield Greater Power).
The propensity of some ransomware ringleaders to vent via posts to Russian-language cybercrime forums, rather than simply taking their earnings and quietly exiting, also suggests they're under increased stress to maintain the pace of operations, if not also their anonymity. "I think the emotions are indeed running high and if law enforcement starts cracking down, we can expect a lot more of these outbursts," Fokker says.






















