Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response
500,000 Android Users Victimized by Malware-Infected App
Text-Coloring App With 'Joker' Strain Was Available on Google Play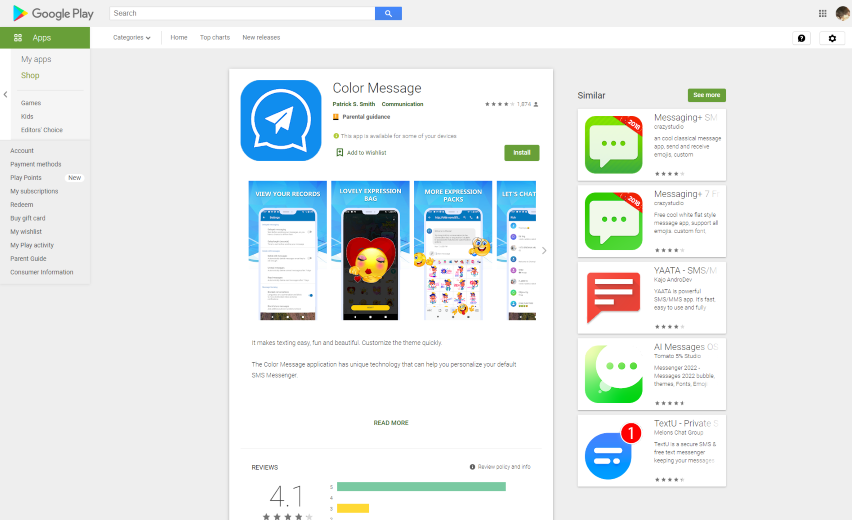
A Trojanized malicious software known as "Joker" malware has made a comeback and was detected in a Google Play app downloaded more than 500,000 times, researchers say.
See Also: Spear Phishing: Top 3 Threats
The Joker malware has reportedly existed since at least 2017, and attackers have used it widely.
Global mobile security company Pradeo discovered that the malicious software had made a comeback via Google Play and says threat actors continue to use it to victimize users worldwide. The researchers for Pradeo say that the malware has propagated across Android and third-party app stores.
More than 500,000 users downloaded the app - called Color Message - that was found to contain the malware. Researchers also say stolen data siphoned through the malicious app appears to link back to servers in Russia, according to the research by Pradeo.
Color Message was designed to offer users the ability to enhance text messaging through emoji use and by blocking junk text messages. But Joker malware causes it to harvest contact information and other sensitive data.
The malware also insidiously subscribes users to a payment system without their knowledge, the researchers say.
The fraudster who reportedly developed the app has been linked to the email address "Kyle.T.Wynne19198@gmail.com" and is said to have created an unbranded blog page to host the app's terms and conditions, as reported by Ars Technica. There, users complained about an inability to unsubscribe and other deceitful activity.
Users were also unaware of the app's performance abilities on the device, according to Ars Technica.
App Removed From Google Play
Ars Technica says it contacted Google to bring attention to the malware in Color Message. Google immediately took the app down from Google Play but did not offer additional comments, the company says.
Roxane Suau, vice president of marketing for Pradeo, who authored a blog post on the findings, tells Information Security Media Group, "Cybersecurity firms have repeatedly discovered the Joker malware hiding in mobile applications available on Google Play."
A Google spokesperson did not immediately respond to ISMG's request for comment.
'Discreet Footprint'
By simulating clicks and intercepting SMS, Joker malware circumvents security measures and connects to the threat actor's command-and-control server. This process then sends user data back to the attacker and downloads other devious components.
A notable feature of Joker attacks, which are difficult to detect and mitigate, is that once the application is installed, it can hide on a user's device.
"By using as little code as possible and thoroughly hiding it, Joker generates a very discreet footprint that can be tricky to detect," according to Pradeo's research.
Similar attacks are sometimes called fleeceware for the scamming tactics developed within the app to rack up payments, although a Wired article says fleeceware attacks only include financial theft, not data theft. The malware's developers trick users into downloading the service, usually by disguising the app as a knockoff of a popular, benign app.
Joker Variants
Different variants of the Joker malware have emerged since its introduction in 2017.
For example, in 2020, dozens of apps were discovered to contain variants of Joker malware and several apps - including digital coloring, camera, a messenger app, and more - in AppGallery, which is Huawei's app store, were discovered in 2021.
Previous apps known to be infected by Joker malware include Safety AppLock, Convenient Scanner 2, Push Message-Texting&SMS, and others, according to Pradeo.
Tatyana Shishkova, an Android malware analyst for Kaspersky, took to Twitter on Thursday to outline other apps infected by Joker. She posted four links to apps in Google Play that were also infected, with a screen capture of the apps.
Mitigation and Detection Strategies
Suau tells ISMG that it is not common to discover malware on the Google Play store. "Finding malware on Google Play does not happen every day, though our security team observed this year an extremely high number of mobile applications accessing and sending users’ data over the network."
She advises security teams to check for indicators of compromise, or IOCs, related to Joker malware, and ensure endpoints - particularly those connecting to corporate networks - are properly secured and monitored.
Victimization by such attacks can be avoided by following best practices, including reading reviews before installation and only installing apps from verified accounts, "as opposed to sketchy developers' accounts," says Suau, who warns security practitioners overseeing corporate devices to remain vigilant for IOCs.