5 Emergency Mitigation Strategies to Combat WannaCry Outbreak
Patch or Perish, and Don't Block Nonsense WannaCry Domain, Experts Warn
Drop everything and patch all Windows devices against the SMB flaw. And above all, don't block the nonsense domain referenced by the WannaCry ransomware outbreak that began infecting tens of thousands of endpoints on May 12.
See Also: The Gorilla Guide to Modern Data Protection
That's just some of the "patch or perish" advice being issued by governments' computer emergency response teams, warning that there could be a flood of new infections of WannaCry - aka WCry, WannCrypto, WanaCrypt0r - when workers return to their desks on the morning of Monday, May 15.
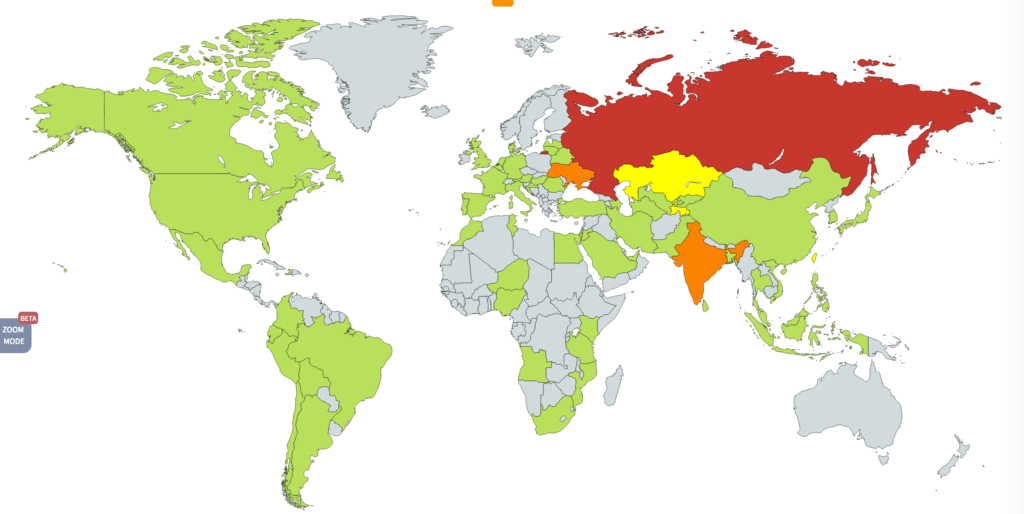
Indeed, Rob Wainwright, director of the EU law enforcement intelligence agency Europol, told the "Preston on Sunday" news program in Britain on May 14 that more than 200,000 endpoints had been infected worldwide by the ransomware, across at least 150 countries, and predicted that many more infections would occur when workers returned to their office the next day (see Responding to WannaCry Ransomware Outbreak).
Infected organizations ranged from Britain's national public health service, the NHS, to Spanish telecommunications firm Telefonica, to shipping giant Fedex, to Russian government servers. Security firm Avast says the main targets of the ransomware appear to be in Russia, Ukraine and Taiwan, but notes that the ransomware includes localized translations in 28 languages - from Bulgarian to Vietnamese.
Don't Block Domain
So far, however, many individuals and organizations in the United States were spared infection when a British security researcher known as "MalwareTech" registered a nonsense domain that the malware used as a check for whether it was installed on a legitimate endpoint. If the malware couldn't look up the domain, then it executed. By registering the domain, however, the security researcher accidentally led all new infections of the ransomware to kill themselves.
Don't block that domain, security experts warn.
"Work done in the security research community has prevented a number of potential compromises," according to security guidance issued by the U.K. National Cyber Security Center. "To benefit from this, a system must be able to resolve and connect to the domain below at the point of compromise: www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com."
The NCSC adds: "Unlike most malware infections, your IT department should not block this domain."
But Alan Woodward, a professor computer security at the University of Surrey who's a cybersecurity adviser to Europol, says that some organizations, including malware blacklisting services, appear to have blocked the domain.
Oh crap! Whoever maintains the UK ISP blacklist needs to act now to remove the wannacry domain - you're doing more harm than good pic.twitter.com/8WJQ76dRuR
— Alan Woodward (@ProfWoodward) May 13, 2017
5 Essential Mitigation Strategies
Computer emergency response teams and security experts say there are five essential WannaCry mitigations that all firms should now have in place:
- Install MS17-010: One way the SMB flaw - targeted to install WannaCry ransomware - can be fixed is for organizations and individuals to install the MS17-010 fix issued by Microsoft in March. "It is critical that you install all available OS updates to prevent getting exploited by the MS17-010 vulnerability. Any systems running a Windows version that did not receive a patch for this vulnerability should be removed from all networks," security firm Malwarebytes warns in a technical analysis of the attacks.
- Install emergency Windows patch: In an unusual move, Microsoft has issued one-off security fixes for three operating systems that it no longer supports: Windows XP, Windows Server 2003 and Windows 8.
- Disable SMBv1: NCSC says that "if it is not possible to apply [either] patch, disable SMBv1," and it refers to guidance from Microsoft for doing so.
- Block SMBv1: Alternately, or in addition, "block SMBv1 ports on network devices" - UDP 137, 138 and TCP 139, 445 - NCSC recommends.
- Shut down: As a last resort, if none of those options are available, it recommends literally pulling the plug. "If these steps are not possible, propagation can be prevented by shutting down vulnerable systems," NCSC says.
Spain's computer emergency response team has also developed and released scripts that can prevent WannaCry from executing on a system, according to Europol's European Cybercrime Center.
Available now: @CCNCERT has developed a tool to prevent the #WannaCry 2.0 #ransomware infection https://t.co/3msScNhe5f
— EC3 (@EC3Europol) May 13, 2017
More Risks to Come
While WannaCry has driven many organizations to put in place emergency SMB patches or mitigations, the risk facing organizations does not just involve this piece of ransomware, security experts warn.
That's because the related attack and code - involving a worm that targets the SMB flaw in Windows to install WannaCry ransomware - has become public. Accordingly, there's nothing to stop any other ransomware gang, of which there are many, from using the SMB-targeting worm to install their own ransomware on endpoints. Furthermore, other analyses of the SMB flaw and potential exploits have also been published by security researchers, for example to the open source penetration testing frameworks Exploit Pack as well as Metasploit.
These penetration testing tools enable security teams to test their own infrastructure for the existence of the flaw. "It should help them with their penetration and other security testing," Woodward at Surrey University tells Information Security Media Group. "I fear not all are doing it."
Of course, the developers behind WannaCry could also easily rewrite their malware to continue targeting Windows PCs with the SMB flaw. On May 14, for example, it appeared that new variants of WannaCry had appeared that checked a different domain than the one spotted by MalwareTech.
So wannacry is morphing - still has "kill switch" but different domain. Is some idiot he editing the original & relaunching ht @benkow_
— Alan Woodward (@ProfWoodward) May 14, 2017
"There's not really much effort for them to change the code and then start over - so there's a good chance they are going to do it, maybe not this weekend but quite likely on Monday morning," MalwareTech told the BBC.




















