3rd Party Risk Management , Data Breach Prevention and Response Summit , Events
Supply Chain Security - The First and Weakest Link in the Chain?

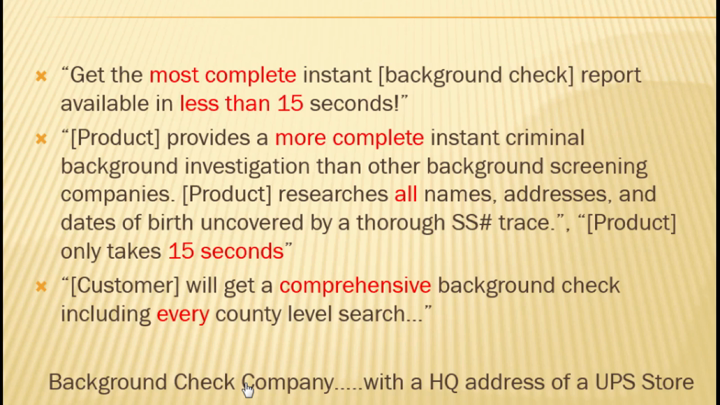
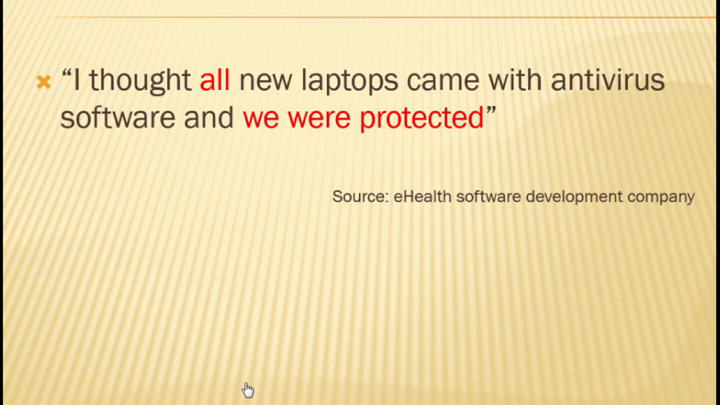
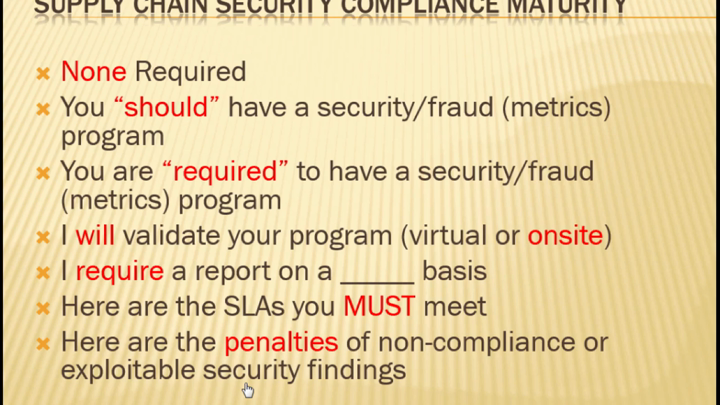
Do you have a supply chain or just vendors? Do any or all of them present a breach potential? We apply massive resources to hardening perimeters and preventing infiltration of our information security systems, but what if our adversaries have a built-in presence and already have a foothold in the software, hardware, people and process components we select to create our infrastructure from day one? In this session we will talk about scoping your supply chain and applying breach avoidance, response understanding and practices to the management of your supply chain. We'll define the various components of the supply chain and discuss its vulnerabilities from both a data breach and fraud perspective. We will also explain the various protection mechanisms and post event response best practices from a seasoned practitioner point of view.
See Also: Expanding Beyond Cybersecurity to Take on Digital Trust
Additional Summit Insight:
Hear from more industry influencers, earn CPE credits, and network with leaders of technology at our global events. Learn more at our Fraud & Breach Prevention Events site.