Data Breach Prevention and Response Summit , Events , Fraud Management & Cybercrime
Phase 3 - Zero-Day Threats, Known Vulnerabilities and Anomaly Detection

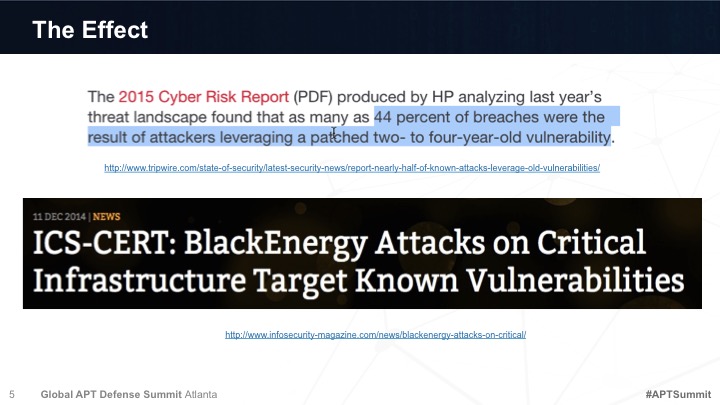
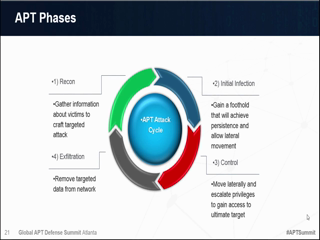
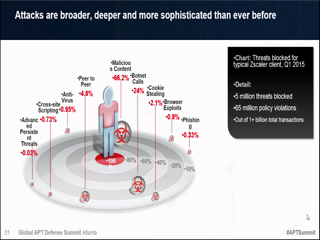
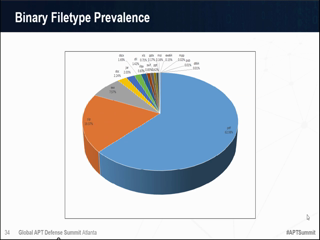
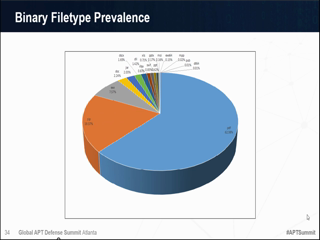
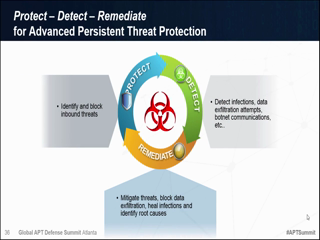
What are the most common mechanisms used in the "Exploit" phase? Many attacks simply take advantage of known vulnerabilities or network weaknesses that have not been addressed, in which case the adversaries have no need to create custom malware. When they are employed, "zero-day" attacks are often very difficult to detect as they exploit hidden or as yet unknown vulnerabilities in applications, operating system features or user accounts, making them difficult to detect. But as these weapons are installed, become resident and establish command-and-control communications, they do create a trail of threat indicators that can be detected, followed and acted upon. This session will discuss some of the known vulnerabilities that are still most commonly exploited, and identify multiple strategies for detecting and responding to zero-day malware, as well as discuss mechanisms such as:
See Also: SamSam: Inside One of the World's Top Forms of Ransomware
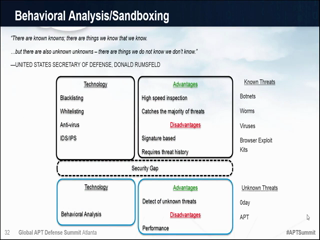
- Behavioral- and signature-based analysis;
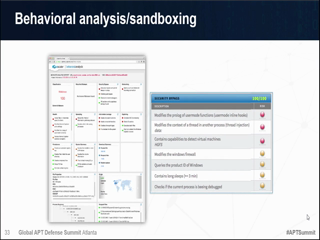
- Virtualization, sandboxing and hardware/CPU-based isolation of suspicious programs and traffic;
- Malware and network anomaly detection, correlation and reporting.
Additional Summit Insight:
Hear from more industry influencers, earn CPE credits, and network with leaders of technology at our global events. Learn more at our Fraud & Breach Prevention Events site.