Trump's Email Servers Dangerously Outdated
Researcher Finds Trump Organization Runs IIS 6.0, Windows Server 2003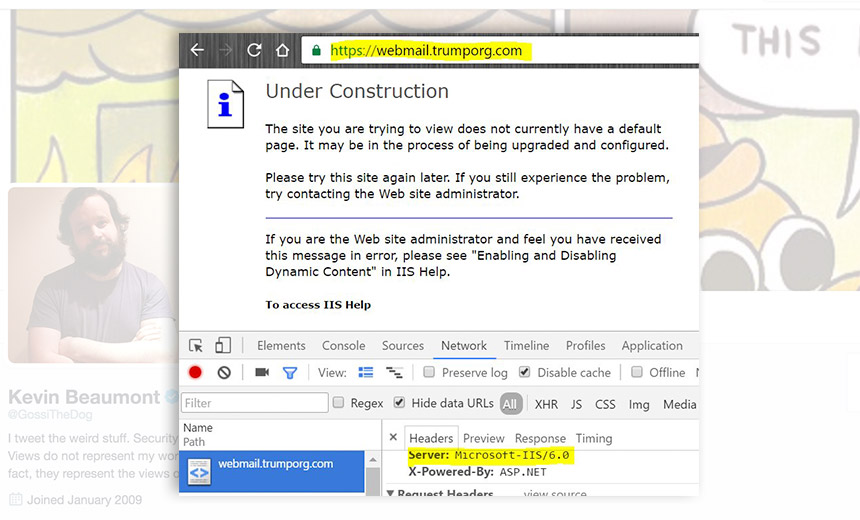
A U.K.-based researcher using public data found that U.S. presidential candidate Donald Trump's business organization runs email servers using decade-old Microsoft software, posing dangerous security risks. In a presidential election where hackers and cybersecurity have played a large role, it's surprising that the findings didn't come to light sooner.
See Also: Deception-Based Threat Detection: Shifting Power to the Defenders
Kevin Beaumont, who lives in Liverpool, investigated websites falling under the umbrella of the Trump Organization, which manages the Republican presidential candidate's real estate, golf and hotel businesses.
Beaumont tweeted a screenshot on Oct. 18 that showed webmail.trumporg.com ran Microsoft's Internet Information Services 6.0, a web server that was part of Windows Server 2003. Microsoft stopped developing security fixes for Windows Server 2003 in July 2015.
It appeared that Trump's email systems were accessible from the web, but did not use multifactor authentication, such as one-time passcodes, Beaumont found. The services also don't have a mobile device management feature.
That's a particularly bad oversight, considering the woes of the Democratic Party. It's believed that hackers acting on behalf of Russia obtained critical party correspondence in part by capturing usernames and passwords. Requiring an additional time-sensitive passcode offers greater security if login credentials have been stolen (see DNC Breach More Severe Than First Believed).
But We Have a Firewall
The Trump Organization couldn't immediately be reached for comment. But Beaumont tweeted a statement released by the organization, which downplayed the findings and offered a questionable explanation of why there isn't a problem.
"The Trump Organization deploys best in class firewall and anti-vulnerability technology with constant 24/7 monitoring," it says. "Our infrastructure is vast and leverages multiple platforms which are consistently monitored and upgraded using current cyber security best practices."
Security experts generally recommend moving to current, supported versions of software. Microsoft gives long lead times for when it plans to retire a product, so companies can budget and prepare to migrate to new platforms. Still, some organizations delay those moves, which weakens their defenses against hackers.
Patching as soon as possible is also recommended. But for unsupported software, there are no fixes. In those cases, firewalls or other security software may be ineffective at stopping an intrusion.
In regard to the Trump Organization's statement, Beaumont writes: "That's a bit like saying it's okay to install WordPress and leave it unpatched forever because there's a firewall."
Trump corp have issued a statement saying it doesn't matter if they run Exchange on Win 2003 internet because they have a firewall. pic.twitter.com/F6FmjFE6nN
— Kevin Beaumont (@GossiTheDog) October 18, 2016
FBI Contacted
After Beaumont began trickling his findings on Twitter, Trump supporters took him to task and apparently contacted law enforcement. "The FBI and Secret Service had a bunch of complaints from angry people who didn't understand what they were reporting," Beaumont writes.
In subsequent tweets, Beaumont clarified how he obtained the information. He didn't probe the servers other than visiting their domain names and using a feature in the Chrome browser that shows the version of software that runs on the site and also viewing Domain Name System records, which are public.
Beaumont's findings are especially ironic given the almost outsized role cybersecurity has played in the election, from the concerns around Hillary Clinton's use of a private email server while serving as secretary of state to suspected Russian meddling in the election.
Trump extensively criticized Clinton's use of a private email server, which she says she regrets. But while the FBI found Clinton and her staff were careless in handling classified information, the agency did not recommend criminal charges. It's unclear if the email server was compromised by hackers.
On Oct. 7, the U.S. formally accused Russia of coordinating the compromise of political figures' email accounts, leading to emails being posted on websites including DCLeaks.com and Wikileaks. The activity could only have been coordinated by senior Russian officials, the Department Of Homeland Security and Office of the Director of National Intelligence asserted. Russia has repeatedly denied involvement (see US Government Accuses Russia of Election Hacking).

















