3rd Party Risk Management , Access Management , Identity & Access Management
3 InfoSec Woes Plaguing Federal Agencies
Deficiencies with Access Control, Configuration Management, Third-Party Oversight
An inspector general's memo that highlights three significant information security deficiencies that have plagued the U.S. Department of Labor for the past five years points out problems that most federal agencies confront.
Labor Assistant Inspector General for Audit Elliot Lewis identifies deficiencies in access controls, configuration management and third-party oversight.
Significant Deficiencies from Department of Labor's Last 11 Semiannual Reports to Congress
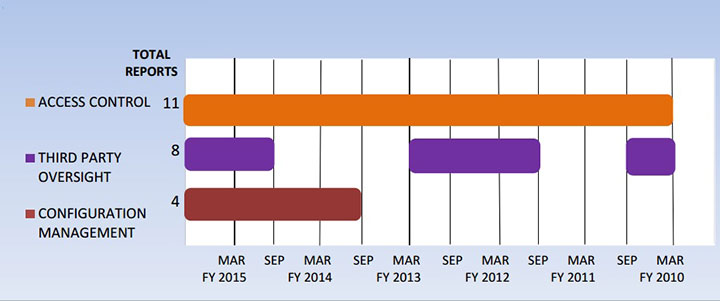
But, as the Government Accountability Office's Gregory Wilshusen says in an interview with Information Security Media Group (click on player above to hear the audio report), shortcomings in those same three areas trouble nearly every other major federal government agency.
"In our FISMA reports, we consistently show that 22, 23 of the 24 major agencies covered by the CFO Act have weaknesses in those areas," says Wilshusen, GAO information security issues director.
This audio report features an explanation of the points Lewis makes in the memo, as well as comments from Wilshusen on their significance to other federal agencies.
The Labor Department has initiated actions to address the deficiencies, Lewis notes in his memo. "However, this trend of recurring deficiencies is indicative of systemic issues that require an overall strengthening of DOL's information security program to prevent future occurrences," he says.
Lewis is responsible for and provides overall leadership to the Office of Audit. He first joined Labor's IG staff in 1991 as assistant director of the Office of Financial Management Audits.
Wilshusen, who joined GAO in 1997, oversees a team that produces GAO's information security audits.



















