Data Loss Prevention (DLP) , Governance & Risk Management , Incident & Breach Response
French Officials Detail 'Fancy Bear' Hack of TV5Monde
Takeaway: Beware Hacked Third-Party Accounts and Weak Active Directory
New details have emerged relating to a hack attack against French broadcaster TV5Monde, which resulted in multiple television channels going dark as well as social media channels run by the broadcaster being hijacked and used to spew apparent jihadist propaganda.
The results of the attack have been well-publicized. In April 2015, online attackers sabotaged French broadcaster TV5Monde, knocking 12 of the broadcaster's channels offline for 18 hours.
But details about how the attack unfolded have just come to light, thanks to a presentation delivered by ANSSI - France's national cybersecurity agency - at an information security symposium held last week in the French city of Rennes. In its presentation, ANSSI thanked TV5Monde for allowing the information about the investigation to be released publicly, saying that unlike many organizations, the broadcaster was doing so to help others to better protect themselves.
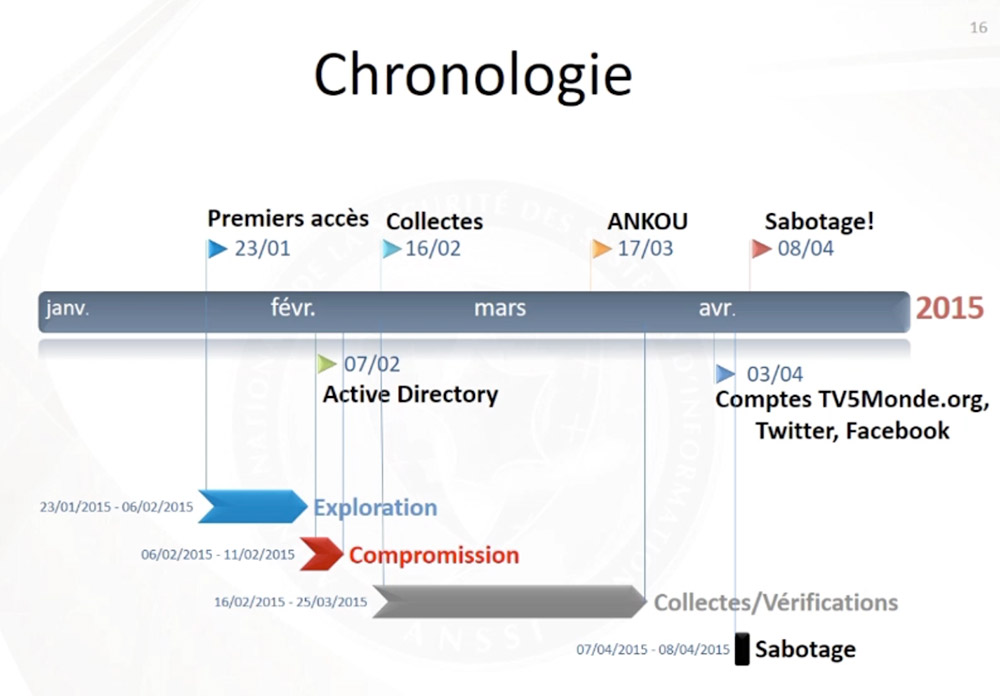
One of the major takeaways from the investigation is that the attacker, or attack group, conducted reconnaissance inside the TV5Monde network for three months, following its initial access, before launching its sabotage operation. Just a few hours prior to that sabotage, which involved knocking multiple channels offline, the attackers compromised multiple TV5Monde social media accounts.
After knocking 12 TV5Monde channels off the air, the hijacked broadcaster's social media accounts - Facebook, Twitter and YouTube - and website began to display jihadist propaganda messages from a previously unknown group, which called itself the CyberCaliphate. Many initial news reports ascribed the takeover to terrorists.
ANSSI says its investigation has concluded that the attackers' goal, from the beginning, was to sabotage TV5Monde's network.
"Once inside TV5's network, the intruders used one of two camera-control servers as a beachhead for privilege escalation," Thomas Rid, a professor of war studies at King's College London, says via Twitter. "To cover the main sabotage op, attackers seem to have planned follow-on ops against internal messaging to slow down TV5's" incident response.
This is "one of the reasons we recommend clients have a separate [communications] channel for incident response," says Brian Honan, who heads Dublin-based information security firm BH Consulting, via Twitter.
APT28 recon apparently started on 23 Jan 2015 (2+ months before main op). Breach allegedly via a VPN through one of TV5's subcontractors. pic.twitter.com/N55I5ohSxM
— Thomas Rid (@RidT) June 11, 2017
Major Takeaways
One of the major takeaways from the TV5Monde investigation is the importance of hardening Active Directory. That's because investigators concluded that attackers were able to create their own admin-level account in Active Directory. After that, attackers gained access to multiple routers and switches and overwrote the devices' firmware, resulting in multiple television channels displaying only a black screen.
Another major takeaway from the investigation was the importance of not only thoroughly documenting IT processes, but restricting access to them as well. For example, investigators concluded that the attackers had accessed the TV5Monde IT department's wiki and used the information it contained to facilitate their sabotage operation.
Clues Point to Fancy Bear
Despite the CyberCaliphate having supposedly hacked TV5Monde, multiple information security firms - including FireEye and Trend Micro - later concluded that the attack appeared to have been launched by the group known variously as APT28, Fancy Bear, Pawn Storm, Sandworm, Sednit and Sofacy. The group is allegedly linked with Russia's military intelligence group, the GRU.
APT28 has also been tied to attacks against the U.S. Democratic National Committee - and potentially also the Republican National Committee - as well as against the German Parliament, the World Anti-Doping Agency the power grid in Ukraine and this year, the French electorate.
TV5Monde Incident Response
The ANSSI presentation provides a blow-by-blow account of the network infiltration and sabotage, as well as the response by the television channel, working with cybersecurity experts inside the national police, the French Ministry of the Interior, ANSSI, the European Union Agency for Network and Information Security, aka ENISA, as well as TV5Monde and other television networks.
For the incident response itself, ANSSI says a team of nine to 15 individuals was involved, comprising one technical coordinator, two to five digital forensic investigators, one malware reverse-engineering expert, two security researchers and three to six auditors.
The incident response team involved in the investigation concluded that the attackers first targeted TV5Monde on Jan. 23, 2015, and accessed a server used by the broadcaster. "One of [the] TV5Monde multimedia servers - used by journalists to send content back - had its RDP port exposed to [the] internet and was using [a] default username/password," French incident response expert Matt Suiche, managing director at Dubai-based Comae Technologies, says in an English-language overview of the French-language ANSSI presentation. "But this machine was not connected to the internal network, and was quickly classified as [a] dead-end by the attacker."
Later, however, attackers returned, using a compromised third-party account that allowed them to connect to the TV5Monde VPN, beginning Feb. 6, investigators found.
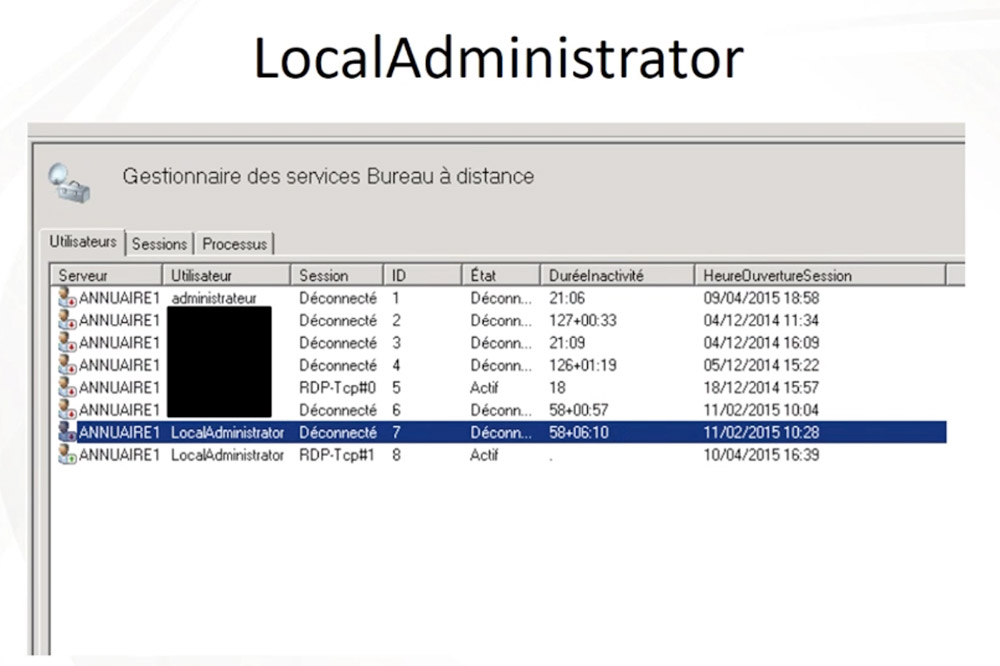
After that, attackers began scanning internal machines connected to an infected endpoint and identified two internal Windows systems that that were used to manage cameras. The attacker then used one of these compromised systems to create a new administrator-level user in Active Director called "LocalAdministator," on Feb. 11, 2015.
The incident response team said this was the first major clue they uncovered about the investigation, saying that it jumped out because all of Active Directory administrator names had been in French.
During the reconnaissance phase of the 2015 attack - from Feb. 16 to March 25 - the attackers mapped the network's IT infrastructure, including searching for various strings - "telnet," "ssh," "video," "compte" [account], "pass," "VPN - and collecting as much related information as possible, including from the IT department's internal wiki, which detailed how login and password was handled, Suiche says.
After that, "the attacker compromised another administrator machine - codenamed: ANKOU - which contains the Remote Access Control (RAT) which was used for the sabotage."
The sabotage consisted of running "destructive commands" - obtained via TACACS logs - that erased switch and router firmware, resulting in black screens for viewers, "except for one new channel that was launched on the same day which was covering the attack from inside," Suiche says.
Important: Keep Logs
The sabotage came to light on a Wednesday - April 8, 2015, to be precise. Incident response began the next day, with investigators amassing about 13 TB in copy images of hard disk, RAM memory and embedded devices targeted by attackers. They also gathered about 300 GB of about 300 GB of compressed TACACS network logs, internal ASA firewall logs as well as various Windows logs, covering desktops, servers and Active Directory.
"ANSSI rightly focuses on the importance of the logs collection but also on memory forensics part, which is very important in such scenarios to keep a frozen state of the infected or machines of interested but easily allows to retrieve information such as the quick-wins described above," Suiche says.
The team was initially worried that attackers may have planted a "logic bomb" inside the TV5Monde network, which could have been used to wipe every system, as was seen in the devastating 2014 wiper malware attack against Sony Pictures Entertainment. Thankfully, however, the team eventually concluded that attackers had not deployed a logic bomb.


















